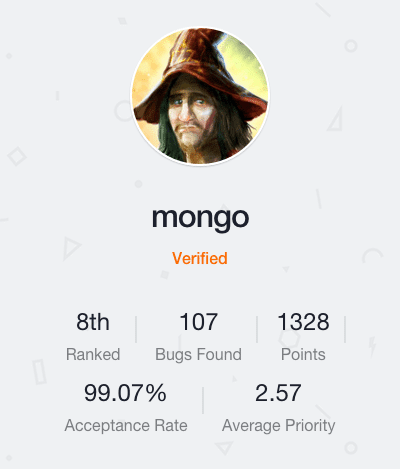
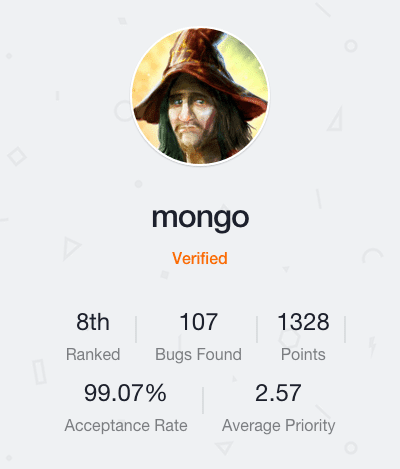
When a new researcher joins our community and quickly climbs the ranks, we take notice. This week’s spotlight is on Mongo, currently ranked 8th on the Bugcrowd Leaderboard with an acceptance rate of 99%. And this is after only 6 months of submitting bugs!
How did you get started in security research? How long have you been doing bug bounty work?
My background is as a developer, though I’ve always been interested in security and low-level programming. I got started in security research about 1.5 years ago when a few friends invited me to play in a Capture-the-Flag (CTF) event. I became passionate about security, started solving as many security challenges as I could, and also reading about security news and publicly disclosed bugs.
My first bug bounty submission was around 6 months ago. I’ve recently started to take it more seriously and invest more time in it.
Do you have a specific focus or specialty that you tend to spend your time on?
I like to hunt for XXE or RCE bugs. I find these classes of bugs are not researched as much (compared to, say, XSS or CSRF), and because they are often harder to find, there is a smaller chance I’ll report something another researcher already reported.
What motivates you to do what you do? What keeps you going?
Contributing towards a safer cyber-world for everyone. The technical challenge aspect attracts me too. Looking for and finding different ways to “break” things has a strange appeal.
Any tips or suggestions that you would give to other bounty hunters?
Spend some time participating in CTF challenges (there is one at least every couple of weeks) and reading the solutions others post online for them after the events are finished. It’s a great way to learn more about vulnerabilities and how to exploit them, in a practical way. Playing with a team on these events is also a great way to make new connections in the field.
Get in early on new bug bounty programs, so you will have a better chance at avoiding duplication on the “easier to find” bugs. Soon after that, focus on the harder bug classes. I’ve found this to be the best way to maximize value to both myself and the owners of bug bounty program.
Finally, for those who have not yet started on bug bounties: dive in, you will find bugs and it will be worth your time. I often talk to people that think public bug bounties are not worth their time because “all the bugs have already been found”. I assure you, that is definitely not the case!
What do you think of the future of bug bounties? Where do you see them going and where would you like to see them go?
I think the future is bright for all involved. Consumers will be safer, companies have another chance to learn about and fix bugs before they become embarrassing news stories, and independent security researchers are paid fairly for their efforts.
I would like to see more bounties on hardware and binary targets; the majority at this point seem to be web targets.