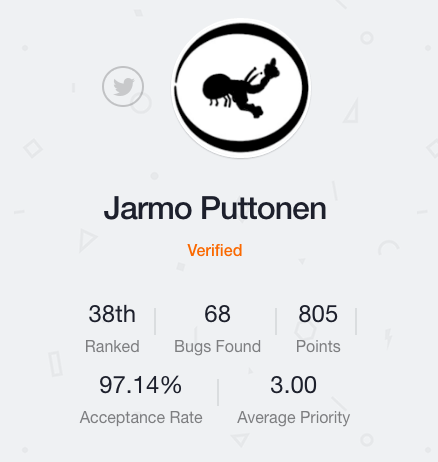
Putsi is #38 on the community leaderboard, with a 97.14% acceptance rate and an average bug priority of 3. Putsi just recently entered the top 40 on Bugcrowd and has had success with many private and public bounty programs on the platform.
Read below for our interview with Putsi and make sure to follow @Putsi on Twitter.
Take us back to your early days, what got you started with technology?
My parents bought me my first computer when I was four years old and I was addicted immediately. Couple years later I was building, breaking and modding computers all the time and decided that I’m going to be a professional video game programmer when I grow up. After I turned 15, I started helping various local companies on IT-problems so that I could get some pocket money.
How did you get started in security research?
Accidentally, actually. In 2013 I was looking for a place where I could do my software engineering internship and randomly ended up in information security R&D internship position. After that I worked for a year as a software engineer but felt that I was more excited during the information security internship. I then started looking for an infosec job and eventually got hired by Insta DefSec to work as an information security specialist.
How long have you been doing bug bounty work?
I joined Bugcrowd on January 2015 but I think that I submitted just one or two bugs during the following months. When I got the infosec job in November 2015 I started doing bug bounties again in my spare time and since then I have submitted about one hundred bugs to Bugcrowd and various independent bounties.
Why do you hack on bug bounties?
I would do more CTFs and other types of infosec stuff but the $$$, kudos and swag keep dragging me back to bug bounties. It’s also nice when a bug that you reported gets fixed and you’ve made the internet a little bit of a safer place.
Do you have a specific security focus or specialty that you tend to spend your time on?
As many others have done, I also started by focusing on the low hanging fruit in web app bounty programs. Lately I have been trying to challenge myself more and have been searching for more critical vulnerabilities. Currently I spend most of my time on RCE, vertical & horizontal privilege escalation, authentication bypass, CSRF, IDOR, SQLi and business logic related bugs. In the future I’ll try to spend more time on bounties that have “binary-application” targets.
Outside of bug bounties, I’m currently spending my time on trying to learn some reverse engineering, malware analyzing and fuzzing skills
What motivates you to do what you do? What keeps you going?
I get motivated by the intense challenge and unpredictability that hacking provides. It’s very rewarding when you have been trying for hours to exploit something and have nearly given up and finally succeed by using some very bizarre gimmick in middle of the night.
I also like to learn new stuff and the field of infosec contains literally infinite amount of stuff to learn and there is never a bug bounty session that doesn’t teach something new.
Any tips or suggestions that you would give to other bounty hunters?
- Keep on learning. Learn from vulnerability disclosures and bug bounty reports. Learn from CTF write-ups. Learn how to use testing tools more efficiently. Learn how to configure and use the applications, frameworks and plugins that you encounter in bounties. Learn to code!
- When doing bounties, #tryharder, #tryharder and #tryharder. It feels awful when you have been looking for hours or days and are sure that there is nothing to be found but there is always something and the persistence usually leads to great discoveries.
- Follow the scene. My primary daily infosec source is Twitter as there are loads of infosec gurus tweeting about news, disclosures, gossip etc. My secondary daily source is Reddit as it has some great infosec subreddits (e.g. /r/netsec, /r/netsecstudents and /r/asknetsec) and loads of sysadmin and programming related subreddits.
Where do you think bug bounties are going in the future?
I think that bug bounties will get more and more popular and will take some resources away from traditional penetration testing as the crowd can do some things a lot more efficiently and a lot more cheaply than a traditional penetration test. I also think that bugs are going to get a lot harder to find as companies are starting to take security more seriously.
Where do you hope to be two years from now?
That’s a difficult question. I hope that I am still doing information security related things as a hobby and at work. I also hope that I’ll get a chance to visit DEFCON and Black Hat USA.