Meet compliance mandates
Align with FDA, DOJ, SEC, CISA BOD 20-01, DORA, and other regulatory guidelines and implement policies and best practices for vulnerability intake, management, and disclosure.
Create a safe harbor for disclosure
Without a clear way to report it, most people won’t bother to tell you about a potentially critical flaw. Make sure they can.
Remediate rapidly
The Bugcrowd Platform integrates with your security and dev processes to ensure that high-impact bugs get fixed, fast.
Build relationships
Engaging with ethical hackers via VDP helps you build relationships for future collaboration on bug bounties and more.
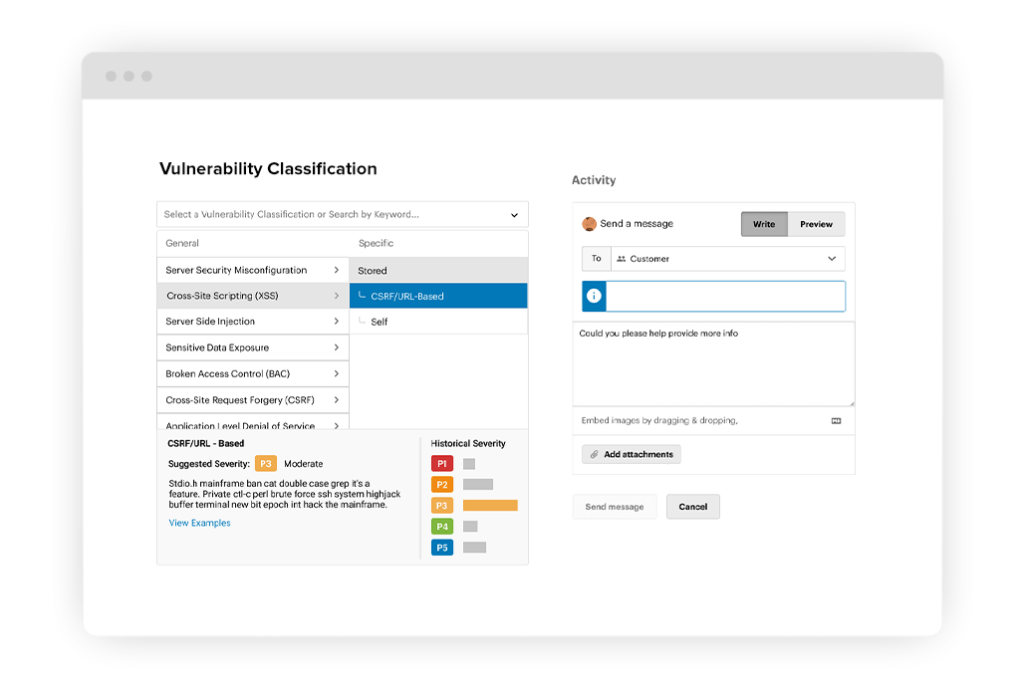
Validation and triage
Engineered triage
Unlike other providers that treat triage like a checkbox, we consider it a key ingredient to customer success. We arm a global, in-house team of specialists with an advanced technology toolbox to enable rapid vulnerability intake, validation, triage, and contextual remediation advice at the Log4J scale—far beyond what competitors can do!
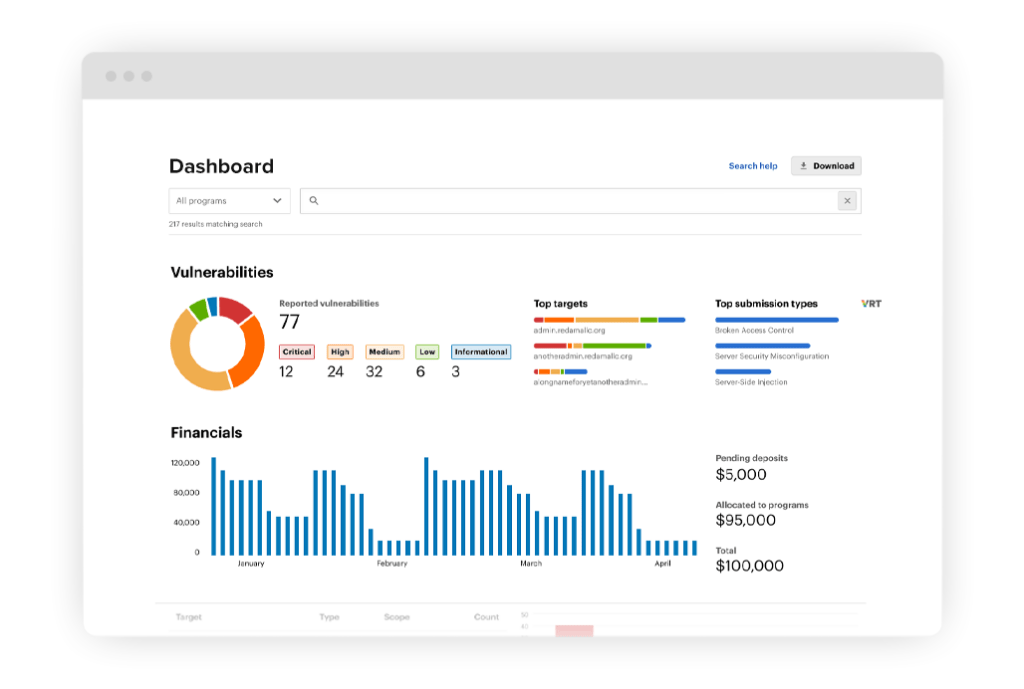
Analytics and reports
Insights for continuous improvement
The Bugcrowd Platform includes a massive security knowledge graph containing millions of data points about vulnerabilities, assets, environments, and skill sets developed over a decade of experience. That data enables dynamic, contextual workflows, AI-powered experiences like CrowdMatchTM, and rich analytics, reports, and recommendations to help you continuously monitor KPIs and improve your security posture.
Step 1: Receive reports
Security researchers around the world review your organization’s defenses from the perspective of an attacker. They probe your cyber defenses for vulnerabilities and report issues through a secure disclosure channel.
Step 2: Validate, triage, and prioritize
The Bugcrowd Platform validates, triages, and prioritizes submissions rapidly, ensuring the direst issues get immediate attention. You always have full visibility into findings through the platform.
Step 3: Review and approve
Your team reviews and confirms triaged submissions. If you need more details, we’ll communicate with the researcher to get the full picture. Bugcrowd is a CVE Numbering Authority (CNA), so you can request official CVE IDs for your vulns, if desired.
Step 4: Remediate and analyze
The Bugcrowd Platform integrates directly with your DevOps and security tools, so triaged findings flow directly into your SDLC for remediation. Use our rich dashboards and reports to benchmark and understand trends.
Sounds like this is the right solution for you?
Get started with a Bugcrowd VDP at your own pace - multiple plans available
BUGCROWD PLATFORM
Don’t get blindsided by unknown attack vectors
The Bugcrowd Security Knowledge Platform helps you continuously find and fix critical vulnerabilities that other approaches miss.
Working as an extension of the Bugcrowd Platform, our global team of security engineers rapidly validates and triages submissions, with P1s often handled within hours
The platform integrates workflows with your existing tools and processes to ensure that applications and APIs are continuously tested before they ship
We match you with the right trusted security researchers for your needs and environment across hundreds of dimensions using machine learning
Our platform applies accumulated knowledge, from over a decade of experience with 1000s of customer solutions, to your assets and goals to optimize outcomes
Built-in security workflows streamline program on-boarding, promote customer and researcher communication, and expedite vulnerability triage, validation, and remediation activities
Shift Left: Flow findings directly into your SDLC

Compliance assurance as you need it





Get started with Bugcrowd
Attackers aren’t waiting, so why should you? See how Bugcrowd can quickly improve your security posture.