Key Facts
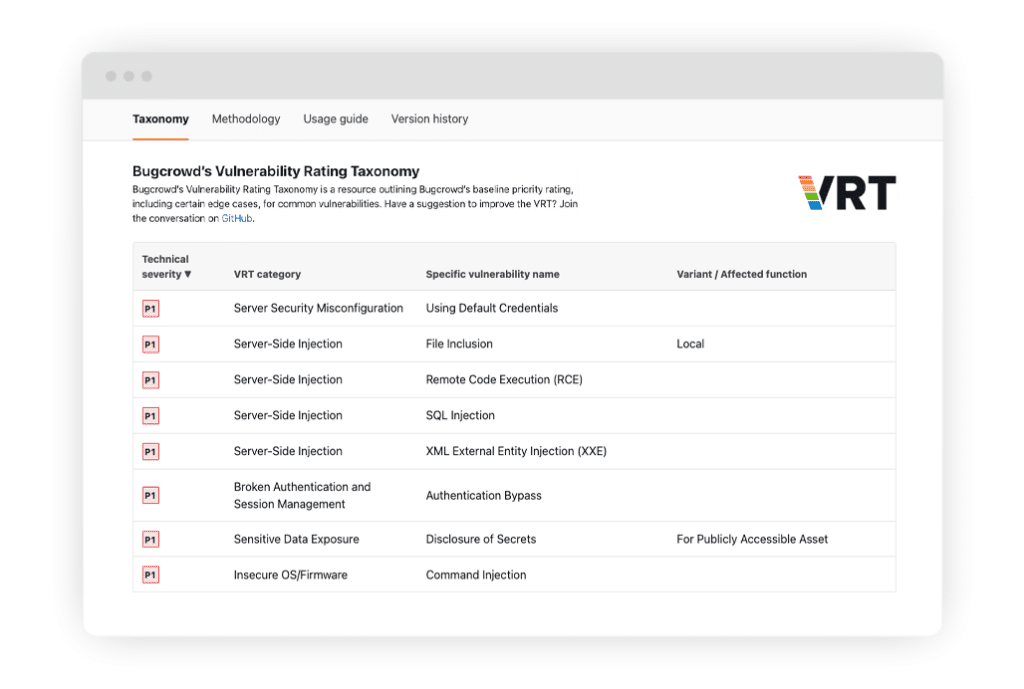
What is VRT?
The Bugcrowd VRT is an open-source, industry-standard taxonomy that aligns customers and researchers on a common set of risk priority ratings for vulns we see often and edge cases. VRT ratings can also be easily converted to CVSS in the platform. Bugcrowd reviews proposed changes to the VRT from the community on a weekly basis.
Customer Benefits
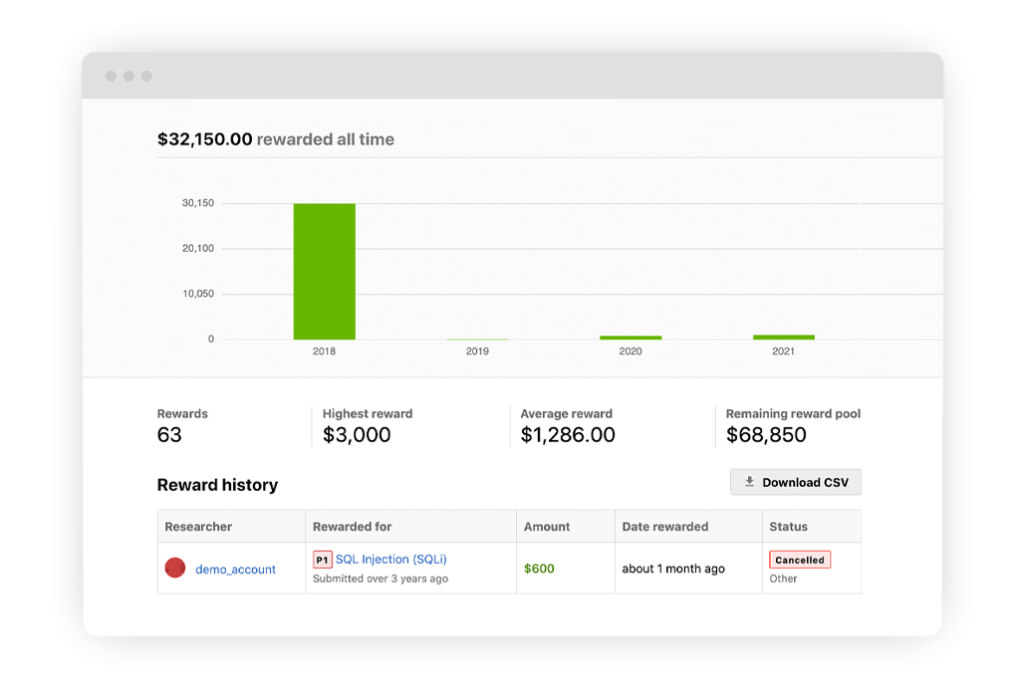
Faster remediation
The VRT helps customers provide clear guidelines and reward ranges to researchers hunting in their programs. When vulnerabilities are ready to be fixed, customers receive VRT-mapped remediation advice to help fix what’s found, faster.
Researcher Benefits
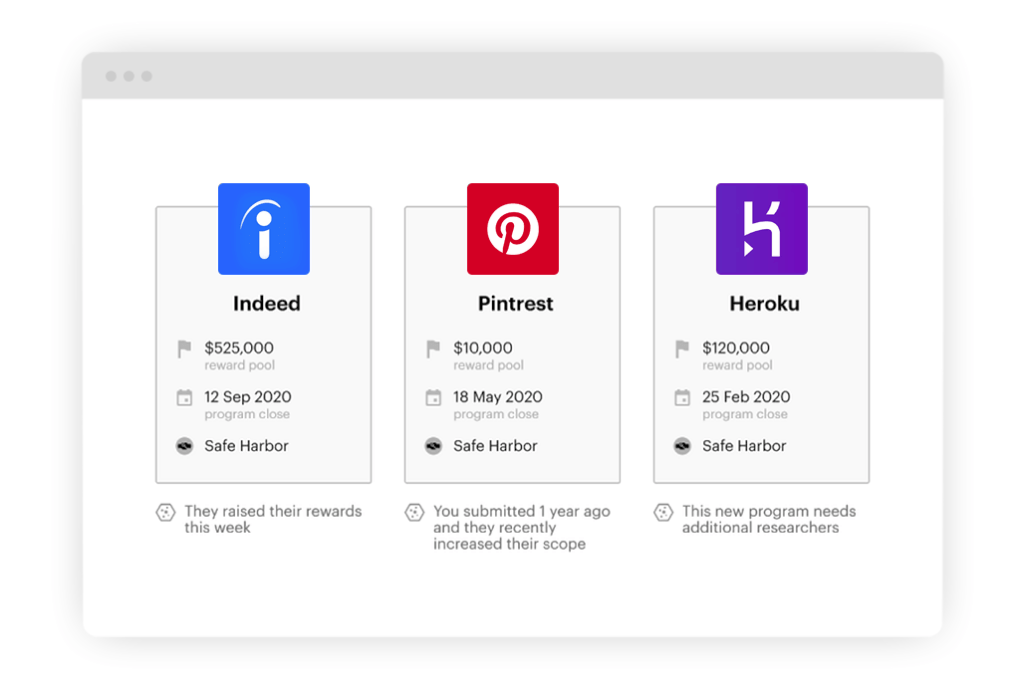
Rewards transparency
Being transparent about vulnerability priority levels helps researchers optimize their time and effort to work on things they value. For that goal, VRT helps researchers focus on specific vulnerability types based on their objective priority to Bugcrowd customers.
BUGCROWD PLATFORM
Don’t get blindsided by unknown attack vectors
The Bugcrowd Security Knowledge Platform helps you continuously find and fix critical vulnerabilities that other approaches miss.
Working as an extension of the Bugcrowd Platform, our global team of security engineers rapidly validates and triages submissions, with P1s often handled within hours
The platform integrates workflows with your existing tools and processes to ensure that applications and APIs are continuously tested before they ship
We match you with the right trusted security researchers for your needs and environment across hundreds of dimensions using machine learning
Our platform applies accumulated knowledge, from over a decade of experience with 1000s of customer solutions, to your assets and goals to optimize outcomes
Built-in security workflows streamline program on-boarding, promote customer and researcher communication, and expedite vulnerability triage, validation, and remediation activities
Shift Left: Flow findings directly into your SDLC

Get started with Bugcrowd
Attackers aren’t waiting, so why should you? See how Bugcrowd can quickly improve your security posture.