Note: This blog is a recap of our latest webinar, “5 Minutes to 50% More Attack Surface” You can access the full recording here.
It’s 11pm. Do you know where your assets are? Do your attackers?
In our latest webinar, Bugcrowd Founder, Chairman, and CTO, Casey Ellis is joined by Jeremiah Grossman of Bit Discovery to discuss how our newfound partnership helps organizations gain visibility and control over previously unknown attack surface in as little as 5 minutes. In case you missed it, here are 5 key takeaways from the session:
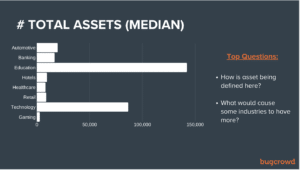
1. It’s not just about looking for vulnerabilities, it’s about knowing where to look: While Equifax is often considered the poster-child for vulnerability scanning, it turns out that wasn’t really the issue. Equifax was actively scanning for theApache Struts vulnerability prior to breach, but with out an up-to-date inventory of assets, they failed to find it where it mattered.

2. Most organizations are “missing” around 40% of their owned assets: Unknown attack surface as a result of either rapid IT expansion, business transformation, M&A, or just complex accounting and management practices has become a real problem for a growing number of organizations across every vertical.
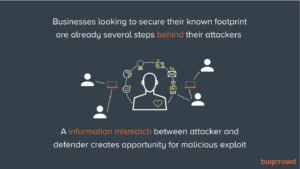
3. An information mismatch between attacker and defender creates opportunity for malicious exploit: While organizations are focused on securing their known digital footprint, most attackers aren’t lining up at the front door. Scanners trained on finding known-knowns in existing asset inventory will never surface the real risks that lie just out of sight. Ironically, it’s often the most simplistic issues like expired certificates or vulnerabilities that have accrued from lack of timely patching that result in the greatest damage.
4. Automation plus human ingenuity trump either alone: Scanners help cover more ground than humans alone can manage in the same amount of time, and– actually that’s hard enough to do well. To expect them to also navigate complex business logic and surface the latest complex vulnerability chains is, well, ludicrous. Humans will always have a leg-up here, but the key is in strategically inserting them in cost and resource efficient ways.
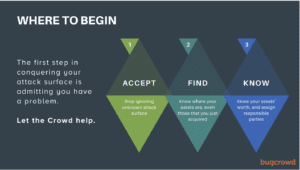
5. Acceptance is the first step in moving on: Most organizations don’t know their entire attack surface. And while that’s expected, it’s really no longer acceptable to customers, partners, and even employees– all groups which stand to lose a lot if an exposed and vulnerable version of WordPress is floating around on the internet. Thanks to Bugcrowd’s Attack Surface Management: Asset Inventory, 5 minutes and a few domain names might be all that stands between you and a more comprehensive view of all of your internet-facing assets.
For more information on securing your entire attack surface, or for information about any of our other products, contact us today!



