This blog first appeared on SEEK’s blog, and is authored by Julian Berton, SEEK security engineer.
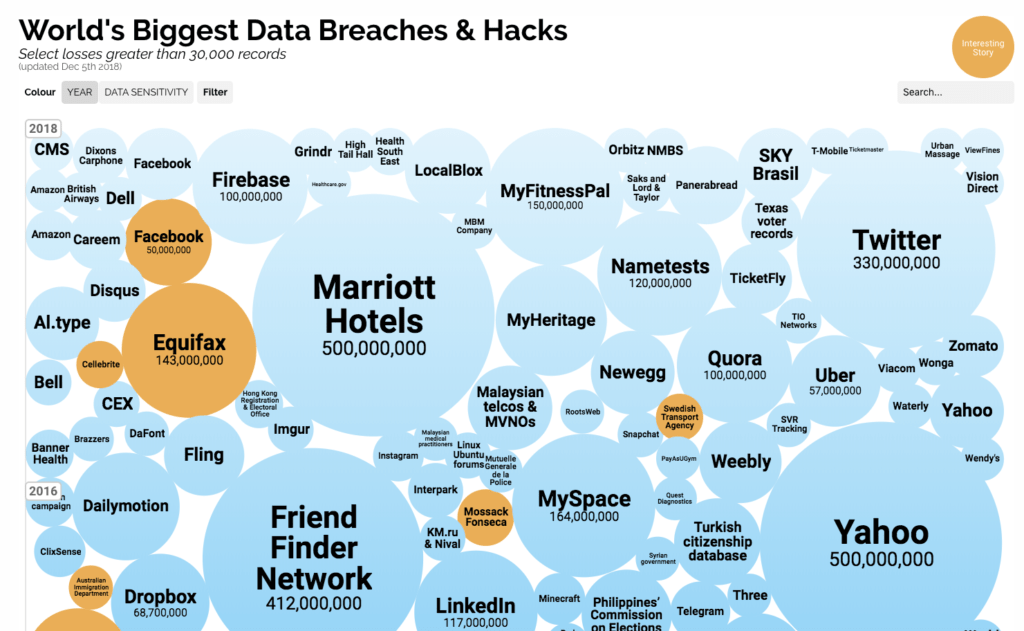
Cyber criminals from around the world are continuously finding new and i̶n̶t̶e̶r̶e̶s̶t̶i̶n̶g̶ terrifying ways of breaking into websites that we rely on every day — stealing our personal information that is typically made public for the world to see! Businesses are breached so often that we now have websites to track these data breaches and to help customers discover if their personal information has been stolen. Personally Identifiable Information (PII) could be used to take over your identity and allow criminals to get into your bank account, apply for credit cards in your name or login to your online accounts using breached website credentials, so it’s critical to keep this information safe!
SEEK has been protecting our customers’ information by running a Vulnerability Disclosure Program. It allows a whitehat security researcher that discovers a bug in our software, to responsibly inform the product team so they can remediate the issue.
Our program has evolved over the last three years, starting out as a static website titled “Reporting Security Vulnerabilities”, that directed researchers to use a security@seek.com.au email address to report vulnerabilities. Now, we have a service that offers researchers monetary rewards and recognition for reporting valid, security vulnerabilities. Commonly called a Bug Bounty Program.
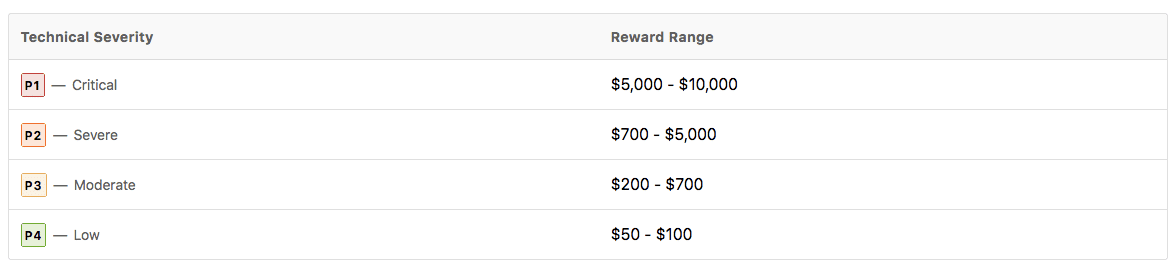
Our private, invite-only Bug Bounty Program, run through Bugcrowd has been a great addition to our software security program, with hundreds of top researchers from around the world selected to participate. So far researchers have reported over 100 valid vulnerabilities within our systems. And we’ve rewarded them with over $100,000 USD. The highest single reward is currently sitting at $10,000 USD, after we increased the rewards for discovering higher risk vulnerabilities.
This year we are taking our Bug Bounty Program public to ensure our websites and services are secure. This means that anyone can now sign up and start testing our websites.
If you want to get involved, head to Bugcrowd and start testing!
For more information on setting up and running a Vulnerability Disclosure Program (VDP) or Bug Bounty Program (BBP), check out the guide here. Or to find out more about how our program has evolved, including examples of bugs submitted, check out the slides and recorded presentation from NDC 2017.