The original post by James Wickett appeared originally on Signal Sciences Lab on 03/24/16.
I have reached the age  where friends are getting roles like CISO or Director of Security or Senior Architect. All important titles with crucial tasks ahead of them. Usually when friends take these roles they immediately realize that they have found themselves in unfamiliar waters. The skills that got them to that role are not the skills they need to succeed.
where friends are getting roles like CISO or Director of Security or Senior Architect. All important titles with crucial tasks ahead of them. Usually when friends take these roles they immediately realize that they have found themselves in unfamiliar waters. The skills that got them to that role are not the skills they need to succeed.
Photo Credit: MSNBC Media
Generally they find themselves dealing with some or all of these problems:
- Their security team is understaffed or undergoing a re-launch or in some cases just starting out.
- The organization operates in a hybrid agile-waterfall manner (read: waterfall SDLC branded as agile).
- There is a segment of the organization (usually a small team) that is pushing towards CI/CD and rapid changes.
- Security is seen as a blocker.
- There is a ton of legacy code or applications with no real current owners and to call it maintenance mode might even be a stretch.
- Security is desired at best or disregarded at worst (usually, it’s a mix).
- The organization’s previous security experience is colored by their engagement with compliance (mostly PCI) and it affects the opinion of security (see previous point).
- Engineers and developers tried to go to OWASP but found out quickly that it wasn’t for them — they deemed it for security professionals.
Some (hopefully not all) of these may sound familiar. When friends have taken these new roles I have two pieces of advice that I give: Break Down Silos and Amplify Feedback Loops
First, Break Down Silos
Break down the silos as much as you can. Security is often caught in the cross-hairs of the siloed organization just by the nature of the role. Often reporting to the CFO or the Legal department rather than the CTO or Engineering department. We can’t control where we are positioned in the org chart — at least not at first. That’s why the first advice is to break down these silos functionally.
Approach development and engineering along with operations and QA with empathy. Find ways to identify with the problems they are trying to solve and be part of their solutions. Since every organization is different, I would rather not give specific guidance, but instead, give some ideas that I have seen work at other companies:
- Attend standup meetings or other agile implementations in the development team.
- Use the tooling of the group you are trying to unite with; say your developers use Jira to track on defects, so when you find a vulnerability you should — no surprise here — use Jira to track it.
- Attend each other’s conferences (devs go with security and security go with devs).
- Host a capture the flag competition for developers with sweet swag and bragging rights.
- Share security data in a self-service way (dashboards, APIs, …) not to be confused with push mechanisms (email, pdf, …).
- Find a security champion in each group and deputize — winners of the capture the flag competition might be a good place to start.
- Pursue automating compliance in the config management stack.
Most of the items on this list are discrete and actionable and the intent is not to complete them just for the sake of doing them — the goal is to break down the organizational barriers between security, operations, and development. These are a means to an end, not an end themselves and in your organization you will need to find ways to bridge groups.
(n.b. I would love to do a series on organizational boundary spanning ideas so leave a comment below or ping me on twitter if you want to be included in that.)
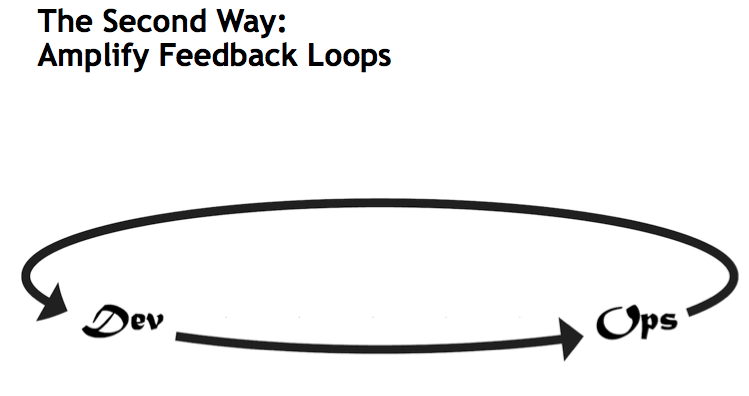
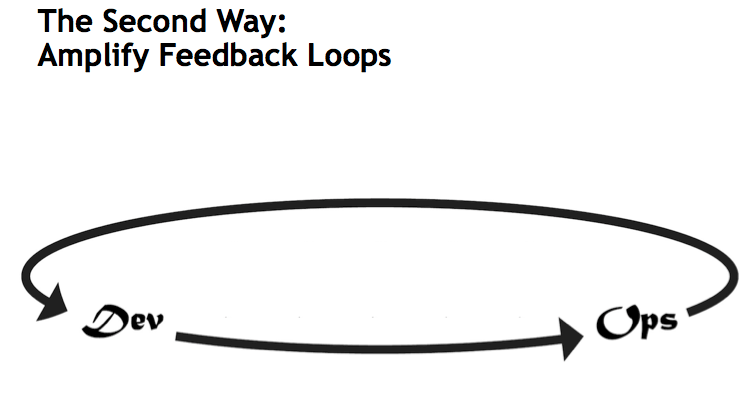
Second, Amplify Feedback Loops
This is inverse to security’s traditional response: Amplify Noise. Often in security, we have the tendency to focus on irrelevant details. We say stuff like “change your password every 90 days” or “don’t click links” or “never join a wireless network outside the company.” This is noise. In the eyes of most people, security’s job is to dream up hypothetical scenarios and then dictate rules based on them. In fact in regard to rules, we love them: the Security Industry has frameworks and security maturity models and reams and reams of guidance all in order to get people to comply with their demands.
So far it hasn’t worked. Rules aren’t motivating.
One of the core principles of DevOps and modern IT practices is to create an environment of continuous experimentation. We need to focus on aligning current IT projects to actual demand. Gene Kim discusses this aspirational level of experimentation in his essay The Three Ways: The Principles Underpinning DevOps. To get to this level of experimentation — what Gene dubs The Third Way — we must first amplify feedback loops (as noted The Second Way).
The Second Way is about creating the right to left feedback loops. The goal of almost any process improvement initiative is to shorten and amplify feedback loops so necessary corrections can be continually made.The outcomes of the Second Way include understanding and responding to all customers, internal and external, shortening and amplifying all feedback loops, and embedding knowledge where we need it.” — Gene Kim
Two Quick Wins to Break down Silos and Amplify Feedback Loops
As a CISO or Director of Security, you are limited in resources. One way to get more resources is to co-opt others in the organization to join your team. Maybe not join your team in an organization chart sense but have them join your team with a shared vision for securing the organization. As Ryan Huber from Slack, you deputize them to care about security.
I think one of the most important ways to get others involved is to answer these two primary questions:
Where are we vulnerable to attacks?
What is actually being attacked?
There are two modern approaches that have proven effective at approaching both of these questions: creating a bug bounty program and instrumenting your web runtime with a NextGen Web App Firewall.
[Disclaimer: This article is co-written by two modern and progressive security companies: Signal Sciences and Bugcrowd. It should be no surprise that we recommend the modern and progressive solutions we provide.]
Bug Bounties
In the modern Internet, bug bounty programs aren’t only for the ultra innovative software companies with deep pockets. Today, bug bounty programs come in many different forms and can work for virtually any company in achieving a specific goal; find critical security bugs before the bad guys do. Crowdsourced security programs encourage thousands of hackers to emulate the behaviors of malicious attackers to provide real results to organizations by utilizing a ‘pay for results’ model. Still, many companies doubt the viability and value in inviting thousands of hackers to the table.
Common Myths Surrounding Bug Bounties
- They’re too high maintenance for a reasonably sized security team to handle
- They only produce noise and low hanging fruit, similar to automated testing methods
- Their quality is low, so they don’t ever find high critical bugs
- I’m putting myself at risk of unauthorized public disclosure
Enter Modern Crowdsourced Security Solutions
Companies like Bugcrowd have made utilizing the ‘the crowd’ easy and incredibly valuable. They work with companies like Pinterest and 99Designs to run public bug bounty programs with their vulnerability platform, Crowdcontrol. They also run private, invite-only programs that tap into a more specialized pool in a more controlled environment, while achieving the same goal of getting high value bugs into the hands of security and dev teams.
Beyond achieving that goal, bug bounties can also address some of the aforementioned challenges present between security and dev teams.
Organizations that utilize bounty programs to the fullest extent are in a position to better understand how and where they’re vulnerable, while at the same time bolstering security awareness and visibility throughout the organization.
Crowdsourced testing and reporting happen in real time, which means security teams can engage in real-time dialogue with their development teams working to implement fixes — breaking down silos. This provides a unique feedback channel that helps both security teams to better understand their attack surface, and engineering teams to write more secure code. By getting more critical bugs in front of your development team faster, you are encouraging the importance and necessity of security — amplifying feedback.
Next Generation Web Application Firewalls (NGWAF)
Web application firewalls have a long history in the landscape of Application Security. They generally have a bad reputation in the industry. Some of the reasons traditional Web App Firewalls have fallen out of favor is:
- They slow down traffic.
- To put them in blocking mode, you first use machine learning mode for a few days which in a Continuous Delivery shop is often untenable.
- Blocking mode is often too restrictive and fraught with false positives thus causing valid traffic to get blocked.
- They are too noisy and not a good way to visualize your attack surface specifically where attacks are happening.
- WAFS are often deployed in a network gateway topology and don’t transfer to the cloud easily.
- For these reasons we needed something different.
Enter NextGen Web App Firewalls (NGWAF)
Signal Sciences has built an NGWAF that overcomes the faults of the traditional WAF.
- Visualizations of attacks in real time.
- Hard guarantees on latency for your important production traffic.
- Cloud-native approach that scales with you and can work in dev, test, and prod
- No tuning or learning mode required.
- Blocking mode with no false positives, in fact 95% of our customers run us in full blocking mode on their production sites.
The NGWAF first and foremost provides visibility across the organization so you can understand where you are getting attacked. This reinforces the role of feedback loops in the modern security organization. Instead of issuing mandates to write secure code, your development and operations teams can see where attackers are targeting in real time — amplifying feedback.
We also believe in breaking down silos and practically that means integrating across teams and tooling. Signal Sciences integrates with products that the rest of your team is using like Hipchat, Slack, Jira, and PagerDuty just to name a few.
Summary
Today’s InfoSec team finds themselves in an unfamiliar landscape of fast delivery times and DevOps organizations, but don’t mistake this as a threat because it is in fact an opportunity for InfoSec. Today, more than ever InfoSec has the chance to integrate into the organization and help build more secure products, services, and teams. Starting with Breaking down Silos and Amplifying Feedback Loops will help you take advantage of this new landscape.
Big shout out to Signal Sciences!