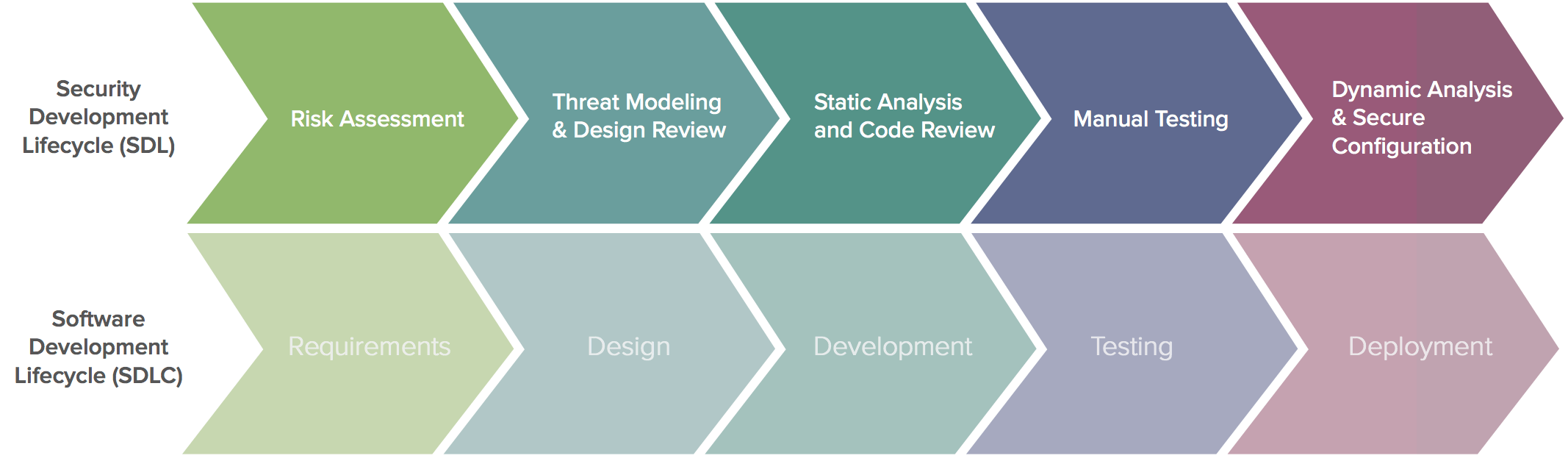
“How does a bug bounty fit into my SDLC?” This is a question we hear all the time. While the obvious answer is that it can augment or replace much of your current manual and automated testing, the actual answer is simpler; “bug bounties fit into and support your SDLC each step of the way.”
A Traditional Take on the SDLC
The SDLC is entrenched in nearly every development organization, yet it has its limitations when it comes to security. With the traditional SDLC model, organizations would hold all security testing until the end of the software development lifecycle, just before the product was released.
As you can imagine, that puts undue pressure on product release dates and can create conflict between departments. For agile development shops, this process is not at all realistic, or effective. Thus, in the past several years, many organizations have ditched their traditional approaches to building software “securely” and have started building security practices throughout the SDLC.
While this “secure” SDLC is a step in the right direction, the current appsec landscape presents four challenges that limit its effectiveness:
- Ballooning attack surfaces that are coming increasingly complex makes it harder for security teams to accurately assess risk and plan accordingly
- Resourcing shortages make it hard to plan and design for security properly
- Traditional security testing methods provide inadequate feedback, leaving holes in production
- Adversaries don’t adhere to an SDLC and are increasingly active and efficient
How can bug bounties help?
Bug bounties align with and support each step of the SDLC, providing more valuable feedback in a more continuous and effective way.
The strength of a bug bounty program lies in the creative and diverse testing pool, and in the cost-effectiveness of the results-driven model. Public or private, continuous or short-term, the bug bounty model scales the benefits of traditional manual testing methods and goes far beyond automated testing methods to deliver real-world security assessment in real time.
So how can bug bounties support and secure your SDLC? From running hundreds of bug bounty programs, we’ve seen the following results from our customers:
- Bug bounties assist in identifying areas within an attack surface of highest risk, and in some cases often uncover unknown weaknesses
- By identifying previously unknown vulnerabilities, bug bounties actually help inform the first steps of the SDLC as it pertains to application security strategy and design
- In this same way, the real-world results that bug bounties produce can also feed into development training programs and support secure-coding best practices
- In the testing and development stages, bug bounties drastically improve processes by offering a dynamic and continuous vulnerability feedback loop and can be deployed in development or production environments
- The pay-for-results model and diverse testing pool combine to improve upon vulnerability scanning which only discovers known issues and penetration testing results which are limited in perception and scale
While bug bounties can be invaluable to bolstering any application security strategy, running them require adequate planning, resources and experience, as well as and the right tools. Bugcrowd’s team of experts and robust platform manage the process for you, making it easy for any organization to implement bug bounty processes seamlessly into your application security strategy and SDLC.
Want to learn more about how a bug bounty can strengthen your SDLC and improve your appsec strategy? Sign up to get our newest guide, released April 5, 2017.
[button link=”/resource/4-reasons-build-bug-bounty-appsec-strategy/?utm_source=website&utm_medium=blog&utm_content=&utm_campaign=4_reasons_appsec”]Download Report[/button]