Note: This is part 2 of a 5-part series in which we examine a smarter approach to attack surface management. Catch up on last week’s post first.
Attack surface is on the rise– but that’s not necessarily a bad thing. As organizations mature, they undertake normal growth activities like business transformation, or M&A. These initiatives expand their web of internet-facing IT, but with limited resources and dispersed accountability, ability to maintain oversight wanes. And in the shadows of…. well… shadow IT, malicious attackers lurk.
Last week we discussed why programmatic attack surface scanners are no match for motivated attackers. In today’s post, we’ll explore how human ingenuity can help, providing every organization with their own Hacker’s Advantage.
The Attack Surface Management Portfolio
While attack surface drift typically occurs over many years of growth and business change, it can also happen suddenly, and unexpectedly. Covid-19-induced “shelter in place” orders have forced a quick shift to fully remote work (where possible). But accelerated timelines for introducing new online services have caused many organizations to shortcut standard launch protocol. And while the arrangement may not last, the impact of mismanaged IT will.
Bugcrowd’s Attack Surface Management portfolio provides two uniquely valuable solutions for discovering, prioritizing, and managing unknown attack surface. Combined, they are the ultimate attack surface management solution.
Attack Surface Management: Asset Risk
Asset Risk is best described as ingenuity-driven asset discovery and prioritization. This on-demand offering leverages the power of our global Crowd of vetted security experts to find and prioritize previously unknown internet-facing attack surface. With access to the latest reconnaissance strategies and tooling from those actively developing them, Asset Risk helps organizations out-hack digital adversaries before they strike.
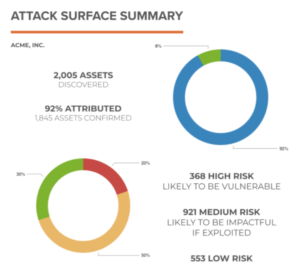 How Asset Risk works:
How Asset Risk works:
- Researcher Activation – Bugcrowd utilizes our unique CrowdMatch technology to locate and activate security researchers best suited for any given reconnaissance program. These individuals are selected by skill, experience, behavior, and trust, and are incentivized in part by the volume and veracity of their findings. This may even include things a scanner is not programmed to surface, like leaked keys, and misconfigured email servers.
- “Seeding” the Search – Organizations supply researchers with information, or seeds, about the known attack surface. Including internal systems and hosting locations can further encourage discovery of things that are inadvertently exposed on the web. Common seeds include:
- Fully Qualified Domain Names (FQDN)
- Classless inter-domain routing Blocks (CIDR)
- IP Addresses and ranges
- Asset Discovery – Commonly called “asset recon”, this process of “hunting” for connected and potentially at-risk assets can include use of bespoke discovery technologies in combination with targeted human intuition. Bugcrowd’s recon experts don’t just find more unique assets,they find more assets full stop, surfacing 50% more on average, than programmatic scanners alone.
- Attribution – Domains may be connected to an organization, without necessarily being owned by the organization. This is something that automated scanners struggle to distinguish, creating excessive noise in final results. Bugcrowd’s human and technology-driven attribution process helps verify ownership prior to reporting, in order to reduce noise and save hours of triage.
- Profiling / Fingerprinting – Researchers profile attributed assets, examining underlying technologies such as content management systems, CRM, e-commerce platforms, advertising networks, marketing tools and analytics, and more. It’s important to note that asset fingerprinting is performed passively, so as not to disturb live systems.
- Prioritization- Unlike Bug Bounty programs, Asset Risk engagements are focused on going “wide,” rather than “deep,” to find unknown, at-risk assets. As these can number in the thousands, prioritization is paramount. Bugcrowd utilizes vulnerability and asset data from over 1,200 managed security programs, as well as live feedback from the Recon team to assign a priority rating to each asset, even without active testing.
- Reporting & Recommendations – The final report outlines what are believed to be the most vulnerable assets, “colored” by risk rating. While some may be destined for decommissioning (or perhaps were already considered offline!), many may require further analysis. Those assets can be rolled into Bug Bounty or Pen Test programs to fully examine indicators of risk including any high priority vulnerabilities.
Attack Surface Management: Asset Inventory
If Asset Risk can be summarized by, “human-powered, software assisted,” Asset Inventory can be thought of as the reverse. Bugcrowd Asset Inventory, which is powered by Bit Discovery, is a software-based continuous scanning solution fueled by an ever-growing pre-indexation of (almost) the entire internet. Organizations can configure alerts, filter inventory, and collaborate with other business units to more effectively manage their internet-facing assets. Additionally, extensive APIs help programmatically ensure compliance and security for the business at large.
How Asset Inventory works:
- Add Domains – Organizations add domains known to belong to their business, in order to train the search engine on locating additional connected assets. Thanks to pre-indexing, asset inventory can be compiled for virtually any organization within a matter of seconds, not weeks. Subdomains are added instantly, while additional “suggested” domains appear with an option to add to existing inventory.
- Technology Fingerprinting – Extensive technology profiling is applied to each asset to better contextualize information and alert on high-impact security risks like open ports and expired SSL/TLS certificates. Hundreds of known features for technologies ranging from marketing and media, to programming and security are used to automatically characterize each individual asset.
- Automate – Continuous discovery keeps organizations apprised of any new or previously unassociated assets, while persistent alerting can inform users when existing inventory becomes at-risk. Public services enable information to be pushed to relevant non-IT business units to bridge compliance and security gaps across the business.
Working Together
While the two solutions can be deployed separately, combining Asset Risk and Asset Inventory enables insights from one to fuel and sharpen the activities of the other. This can improve inventory accuracy, better inform priority rankings, and more rapidly reduce risk across the business.

For more on how technology-backed human ingenuity plays a crucial role in staying ahead of malicious attackers, stay tuned for next week’s blog, or contact us today!



