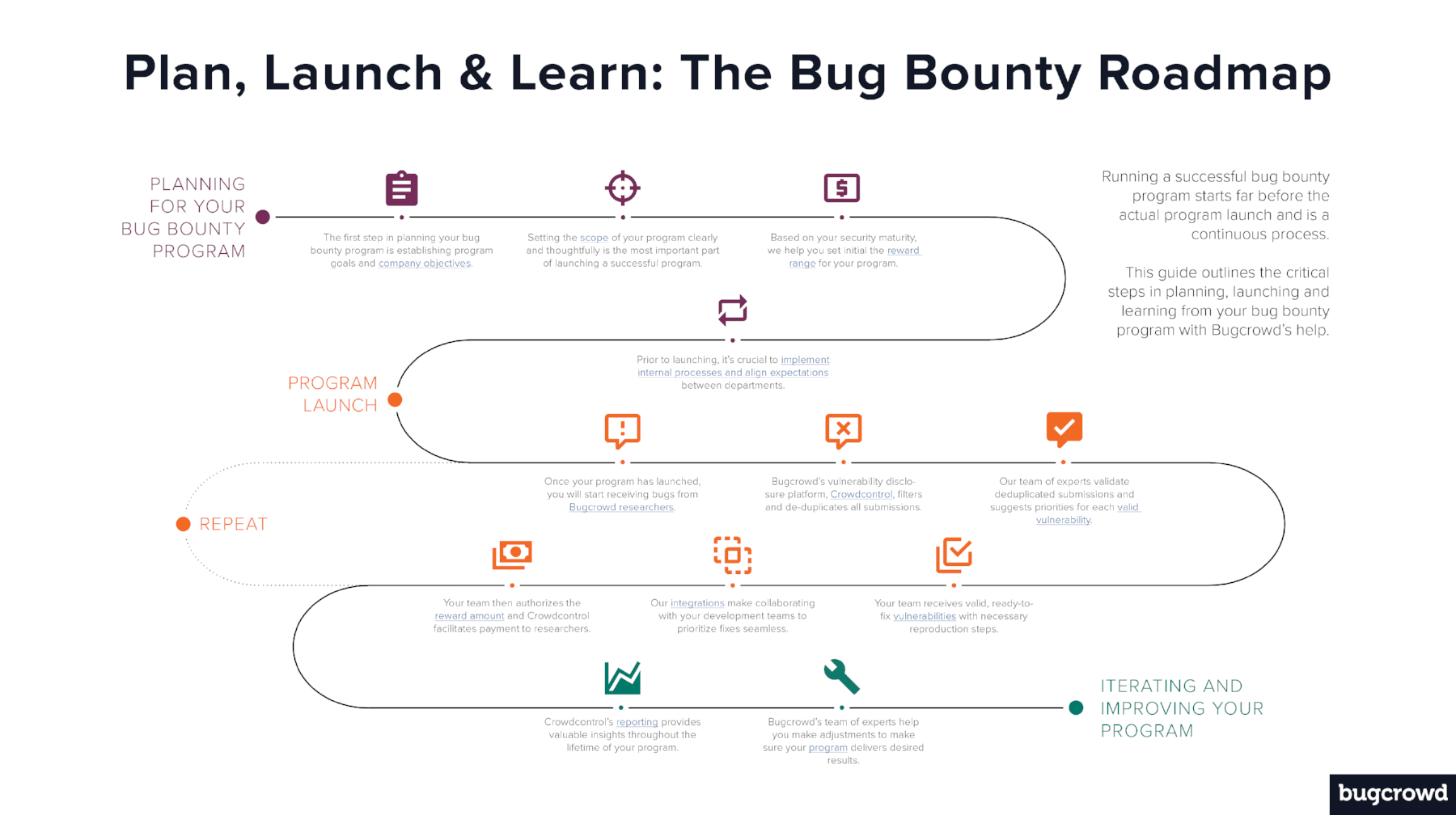
The bug bounty lifecycle is a very fluid process, from strategic planning to program launch to learning from and iterating your program. Get the illustrated guide below:
The success of any bug bounty program is determined far before the actual launch. The pre-launch planning and logistics of a bug bounty program will greatly increase the likelihood for long-term success. This post will explore the key elements of this process, and guide you in the right direction to dive deeper on each point.
#1: Planning for business objectives
Whether you have an active bug bounty program or are looking to implement one, you probably know how working with the bug hunting community can support your organization. Many of the common reasons our customers implement bug bounty programs range from improving overall security testing programs to boosting security marketing and PR.
Learn more about how bug bounties solve many common business challenges >
Determining your business objectives will inform what kind of program to run, what your rewards range will be, what you’re testing and more. Communicating these objectives early and often will also help align internal resources.
#2: Setting program testing scope
Based on the qualifications above, Bugcrowd helps all of our customers set testing scope. In its simplest form, the scope tells the researchers what they can and cannot test – which is paramount to getting the results you want from your bounty program. Some major considerations are:
- Leave nothing up to interpretation
- Know and understand your attack surface
- Prioritize targets clearly
It is important you to define what can be tested clearly and thoughtfully, and identify the focus areas of your bug bounty program.
Learn more about setting up a clear, thoughtful scope >
#3: Setting the initial reward range
Bug bounty programs largely center around rewards–whether that’s Kudos points or cash. We help your organization set the right reward range with consideration to your business requirements and objectives. This step is important in attracting the right talent and attention to your program.
Our ‘Defensive Vulnerability Pricing Model’ defines the market rate for vulnerabilities based on organizational security maturity and bug priority to provide a baseline range to get your program started.
Learn more about setting your reward range >
#4 Aligning internal resources
Lastly, make sure that internal resources are ready and aligned.
In addition to ensuring that you have the essential resources to implement and run a bug bounty program from a technical standpoint, it is equally important to familiarize the entire organization with implications. Bug bounty programs touch much of any organization–from security and engineering functions to even sales and marketing roles.
Learn more about getting your organization ready for a bug bounty program >
These are the first few steps in launching a successful bug bounty program. In the upcoming weeks we will explore the keys to designing and running a successful long-term bug bounty program. To learn more about how bug bounty programs can support your SDL/SDLC, download our recent guide ‘4 Reasons to Build a Bug Bounty into your AppSec Strategy.’