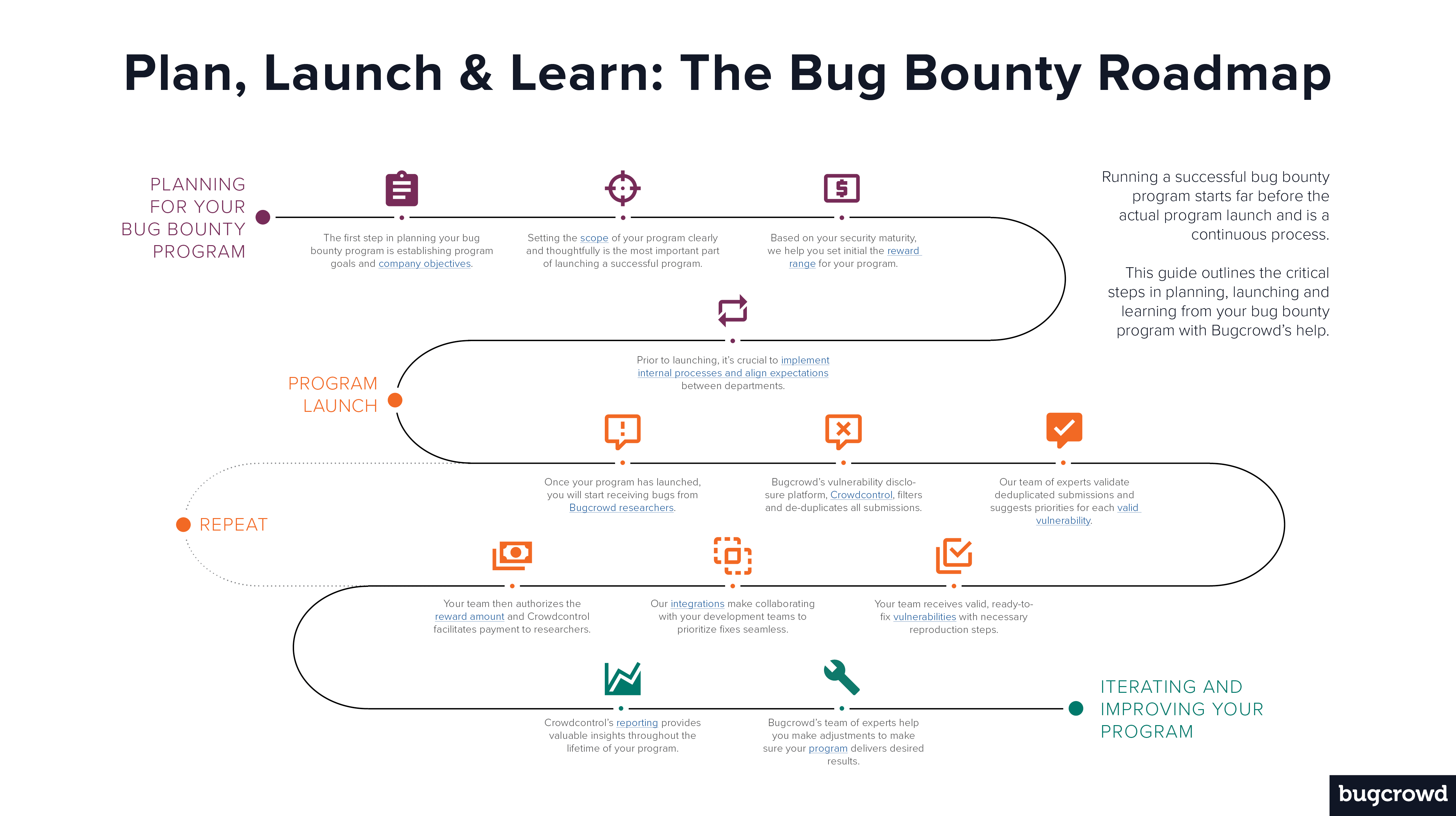
The bug bounty lifecycle is a very fluid process, from strategic planning and program launch to learning from and iterating your program. Get the illustrated guide below:
Last week we talked about the second part of running a successful bug bounty program–the actual program launch. Now that your program is off the ground, you’ve received submissions, and have worked with Bugcrowd’s team of experts to prioritize and reward submissions, the work doesn’t stop.
The bug bounty roadmap is never ending and requires periodic updates; Bugcrowd supports all customers from start to finish. This post will dive into what to expect after you’ve launched a bug bounty program and have been running it for any period of time.
#1: Insightful reporting
All Bugcrowd customers have access to our Crowdcontrol platform which not only manages the submission workflow as discussed in the previous post but also makes it easy to garner valuable insights. Throughout your program–public or private–your team can see how much is being spent, which areas are receiving the most activity, and what bugs are most common.
Learn more about Crowdcontrol’s insightful reporting >
#2: Making program adjustments
It’s crucial to be well-informed as you evolve your program, and Bugcrowd’s Account Management team adds a layer of support in helping you carry out the right adjustments. Bug bounty owners should always be aware of the fact that each program is competing for the attention of the community. While program launches naturally receive a high volume of submissions, the most successful programs work to maintain this activity over time by adjusting the variables at hand such as scope, rewards, and marketing activity.
Adjusting scope
As most players in the bug bounty space know, the bounty scope is essential to each bug bounty program. We’ve already addressed many of the considerations to take when writing your program’s scope, but you should note that the bounty scope is not set in concrete, and should be reevaluated throughout the lifetime of your program.
For example, you may want to remove targets that become less critical to your business over time. On the other hand, you may want to add new products or third-party applications to your scope to increase interest within the community and increase activity across your attack surface. Related to this topic are focus areas, and adjusting target-specific rewards, as discussed below.
Adjusting rewards
We encourage all of our customers to adopt a ‘crawl-walk-run’ approach to their bounty programs. That often means starting private, transitioning to public, and over time increasing rewards. Our team of experts advises the adjustments of awards every step of the way, and we vehemently believe that to maintain activity, activate various groups of researchers, and to continue receiving high-value results, rewards increases are crucial.
Learn more about Bugcrowd’s reward recommendations >
Marketing outreach
In addition to adjusting your bounty brief, which triggers program notifications, we also recommend spending some time communicating with the community. Whether it’s a tweet, a blog post, or a full-fledged marketing campaign, public exposure is a sure way to receive attention. Many of our customers, including Indeed, Jet.com, Canvas, and Fitbit have adopted this tactic to both encourage focused testing and increase overall visibility.
The Bugcrowd team has provided years of support for organizations looking to maintain their relationships with the researcher community and aligning expectations in the long run.
All of these steps are important to keep in mind not only as you iterate upon your program, but as you launch as well. It can help put things into perspective as you address each step of the bug bounty process including…
- Setting business objectives
- Defining your scope
- Setting your reward range
- Managing the vulnerability workflow
In short, bug bounties are living organisms that benefit largely from constant iteration and attention. To learn more about how bug bounty programs can support your SDL/SDLC, download our recent guide ‘4 Reasons to Build a Bug Bounty into your AppSec Strategy.’