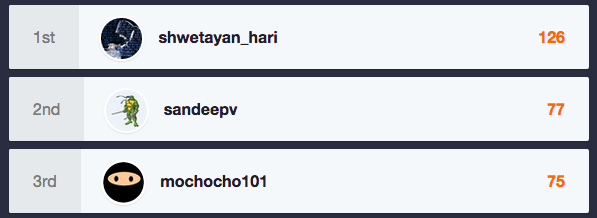
It is time for the June 2015 Hall of Fame, and this month was a close race for the top 3 spots with just 2 points between 2nd and 3rd place. To thank these individuals for their hard work, Bugcrowd is pleased to announce the following researchers will receive June 2015 performance bonuses:
1. shwetayan_hari – 126 points – $2,500 bonus
2. sandeepv – 77 points – $1,500 bonus
3. mochocho101 – 75 points – $1,000 bonus
Want to see your name in the Hall of Fame?
How does a researcher earn Kudos points? High severity bugs earn the most points- see below for the points break down! A great way to do this is to get invited to private bug bounty programs as well as work on public programs. Recently our Senior Director of Research Operations outlined how to get chosen for more private programs.
A Look At Private Program Invites
Thanks again to all Bugcrowd researchers for all of their hard work in June. We can’t wait to see who is in the Hall of Fame for July!
—–
P1 – CRITICAL – 20 points
Vulnerabilities that cause a privilege escalation on the platform from unprivileged to admin, allows remote code execution, financial theft, etc. Examples: Remote Code Execution, Vertical Authentication bypass, SSRF, XXE, SQL Injection, User authentication bypass
P2 – HIGH – 15 points
Vulnerabilities that affect the security of the platform including the processes it supports. Examples: Lateral authentication bypass, Stored XSS, some CSRF depending on impact
P3 – MEDIUM – 10 points
Vulnerabilities that affect multiple users, and require little or no user interaction to trigger. Examples: Reflective XSS, Direct object reference, URL Redirect, some CSRF depending on impact
P4 – LOW – 5 points
Issues that affect singular users and require interaction or significant prerequisites (MitM) to trigger. Examples: Common flaws, Debug information, Mixed Content
P5 – BIZ ACCEPTED RISK – 2 points
Non-exploitable weaknesses and “won’t fix” vulnerabilities. Examples: Best practices, mitigations, issues that are by design or acceptable business risk to the customer such as use of CAPTCHAS.