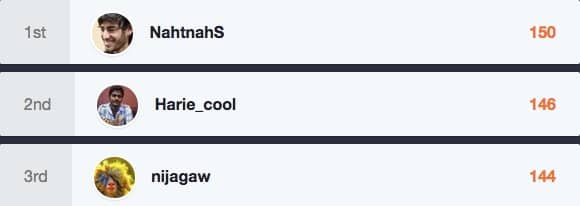
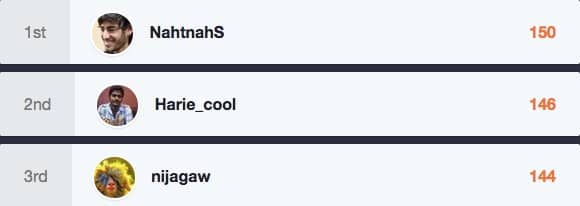
It is time for the May 2015 Hall of Fame, and this month was a close race for the top 3 spots with just 8 points between 1st and 3rd place. To thank these individuals for their hard work, Bugcrowd is pleased to announce they’ll receive performance bonuses.
1.NahtnahS – 152 points – $2,500 bonus
2. Harie_cool – 146 points – $1,500 bonus
3. nijagaw – 144 points – $1,000 bonus
How does a researcher earn Kudos points? High severity bugs earn the most points, which is how NahtnahS got to the top – he made some great P1 and P2 submissions. Bugcrowd’s general guidelines for vulnerability priorities and Kudos points are:
P1 – CRITICAL – 20 points
Vulnerabilities that cause a privilege escalation on the platform from unprivileged to admin, allows remote code execution, financial theft, etc. Examples: Remote Code Execution, Vertical Authentication bypass, SSRF, XXE, SQL Injection, User authentication bypass
P2 – HIGH – 15 points
Vulnerabilities that affect the security of the platform including the processes it supports. Examples: Lateral authentication bypass, Stored XSS, some CSRF depending on impact
P3 – MEDIUM – 10 points
Vulnerabilities that affect multiple users, and require little or no user interaction to trigger. Examples: Reflective XSS, Direct object reference, URL Redirect, some CSRF depending on impact
P4 – LOW – 5 points
Issues that affect singular users and require interaction or significant prerequisites (MitM) to trigger. Examples: Common flaws, Debug information, Mixed Content
P5 – BIZ ACCEPTED RISK – 2 points
Non-exploitable weaknesses and “won’t fix” vulnerabilities. Examples: Best practices, mitigations, issues that are by design or acceptable business risk to the customer such as use of CAPTCHAS.
Great work in May!