Earlier today we joined Jake Kouns, CISO of Risk Based Security, and Christine Gadsby, Director of Product Security at BlackBerry for a guest webcast. They gave their Black Hat 2016 talk ‘OSS Security Maturity: Time to Put on Your Big Boy Pants’ which analyzes the real risks of using OSS and the best way to manage its use within your organization.
This post is a high-level review of that presentation–you can watch the recording here and download their slides here.
OSS Security Issues, Vulnerabilities & Liability:
- In general, the vast majority of organizations using OSS believe that it improves efficiency, interoperability, and innovation. They encourage the use of OSS and participation in open source projects.
- Its widespread use is born out of the desire for all things ‘better, faster, cheaper,’ which presents risks that organizations are either unaware of or uncertain of how to address.
- The problem lies in the statistics around the existence of and maintenance of security processes and controls around OSS.
- Kouns provides several case studies of vulnerabilities in third-party libraries across several products that demonstrate the importance of investigating actual impact against your different products
- Evaluate OSS before usage, reviewing various factors to evaluate if a particular product or library should be used within your organization, including vulnerability metrics like time to patch
- With that information, weigh the costs and risks associated with using that code
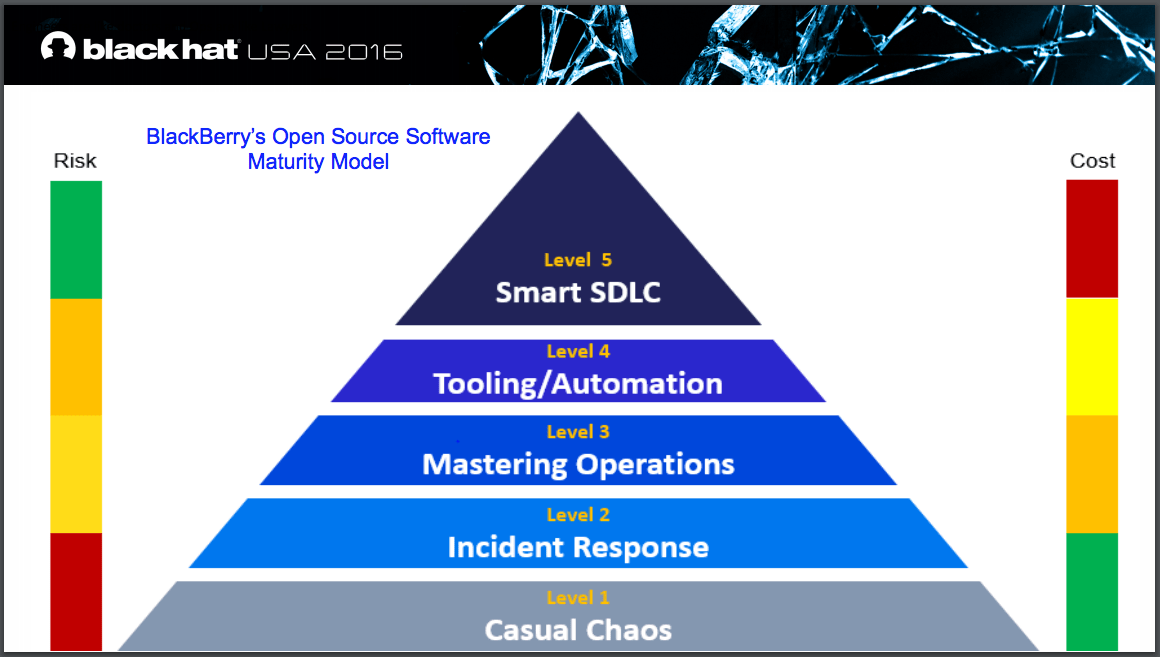
How did BlackBerry Do That?
- Level 1 is incredibly cost effective–because no resources are being spent–but incredibly risky with no real response processes in place
- Level 2 is where your incident response is formed. Your software bill of materials is written, you start to understand your open source spread and start investigating and tracking public vulnerabilities in OSS.
- Level 3 is when cultural advancements are starting to occur between dev and security teams as OSS vulnerability intelligence is proactively gathered. In this level, organizations start understanding how those vulnerabilities impact different products, appropriately prioritizing the implementing of those fixes and start building a relationship with researcher community.
- Level 4 is when all of that intel and processes are automated (watch the webcast to learn about some of BlackBerry’s custom tooling) to use vulnerability data proactively, drive efficient vulnerability handling and communication about customer protection. In this level, OSS risks and costs will have increased visibility internally, which should help influence future decisions.
- Level 5 is when you’re fully using your OSS security intelligence. Now that you’ve gathered intelligence, automated it, and optimized processes, to empower your dev team to make better OSS decisions. Secure and simplify your attack surface by understanding risks, ROI and making smarter OSS decisions.
So Why Do we Care About OSS Security?
This presentation follows our recent webcast by Kymberlee Price on building useful and practical product security incident response teams and processes, an extended version of the presentation she gave during Black Hat 2016, titled ‘Building a Product Security Incident Response Team: Learnings from the Hivemind.’ In that presentation, Kymberlee outlines some frameworks, processes, and ideas to consider when setting up a PSIRT, touching on the additional responsibility and necessary processes when dealing with OSS.
Why do we care? Working with the security research community to find bugs faster and more seamlessly is crucial to product security, and crucial when utilizing OSS. Bug bounties and responsible disclosure policies referred to in Level 3 of BlackBerry’s Open Source Software Maturity Model, are a fantastic way to build that relationship.
For more in-depth context on these challenges and this custom OSS Maturity model with additional examples and considerations, watch the webcast, and feel free to reach out to Jake and Christine with any questions.