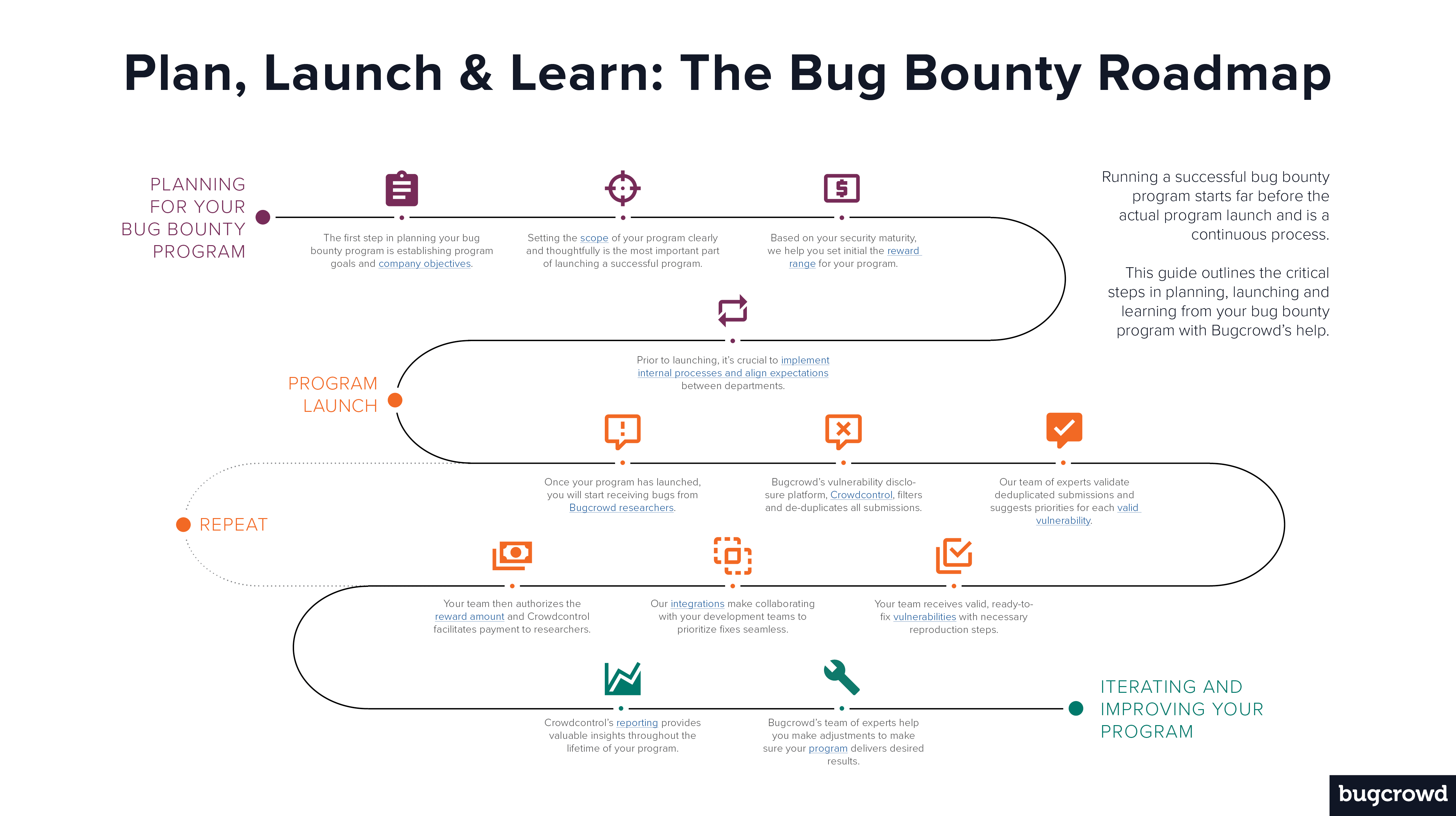
To run a successful and mutually beneficial bug bounty program, the work starts long before you launch your program and is a continuous learning experience.
Simply put, your bounty program can be broken into three main stages: (1) planning and strategy, (2) launching and running your program, and (3) learning from and iterating upon your program. The graphic below outlines the steps involved in each of those stages.
Bugcrowd works closely with security teams of all kinds and sizes throughout this sometimes non-linear process, making recommendations upfront and taking care of much of the heavy lifting.
In the coming weeks, we’ll be taking a deep dive into each of these steps, as well as exploring how you can integrate a bug bounty into your security development lifecycle.