Nessus® Vulnerability Scanner
The Nessus vulnerability scanner is a remote security scanner from Tenable, Inc. Nessus scans a computer and then generates alerts if vulnerabilities are discovered. Nessus runs over 1,000+ checks to see if vulnerabilities exist.
First, you need to install Nessus. There are instructions on the Tenable website that show you how to navigate to the Nessus package file, start the installation, complete the Windows InstallShield Wizard, and install WinPcap.
There are several basic steps to run a Nessus scan. First, you need to launch Nessus. Then in the top navigation bar, you click SCANS. It will take you to the My Scans page, where you will click the New Scan button. Nessus provides a wide variety of templates you can use. You will select the one you want. Scan settings can be configured to refine parameters as required. The template is based upon a scan or policy. These can be configured in the scan’s settings or in a policy from which you create scans. If you configure a setting in a policy, then that setting will apply to all of the scans you make from that policy. You will also want to look at the Discovery, Assessment, Report, and Advanced settings default parameters to see if they fit your environment.
Reviewing Nessus Vulnerability Scanner Results
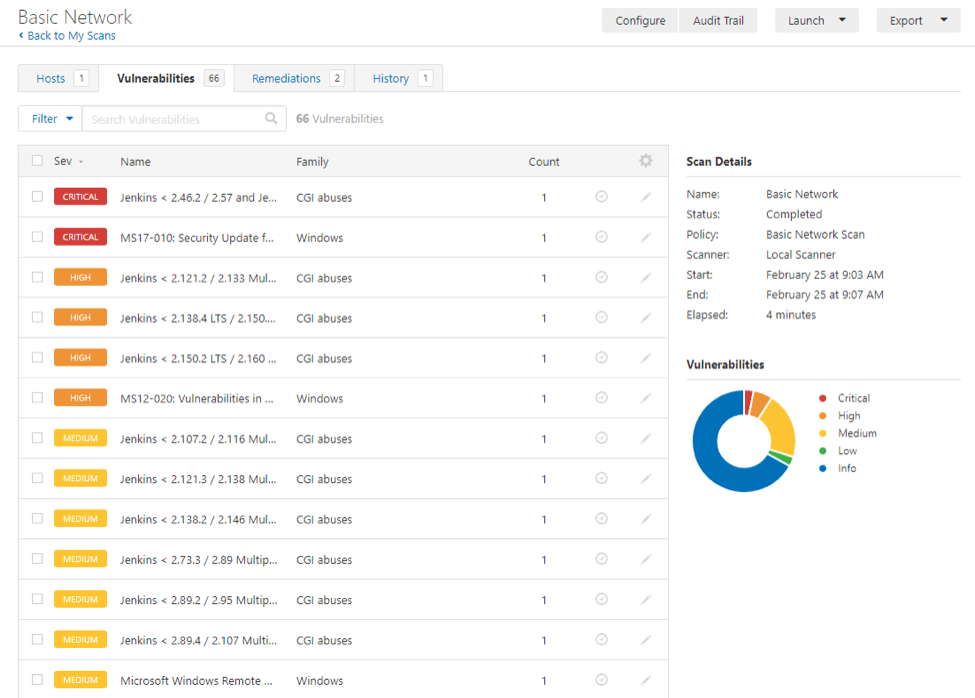
Then you want to review the results of the scan to better understand your vulnerabilities. You can select a host view, a vulnerability view, a remediation view, a notes view, and a history view. Now you can, in turn, report the vulnerabilities to your team. You may want to export the results into a .CSV file, an HTML file, or a PDF file.
Nessus works by testing each port on a computer system, identifying which services are running, and then testing each of these services to detect vulnerabilities. Nessus can be installed on one computer and then can be used to test many other computers.
Nessus also provides for excellent extensibility. You can use the Nessus scripting language so you can write tests very specific to your system. Nessus also provides for a variety of plug-ins which are written in the Nessus Attack Scripting Language (NASL). The plug-ins include vulnerability data, concise information on recommended remediation, and an algorithm to allow for further testing of the security issue. Examples of plug-ins are here: https://www.tenable.com/plugins
Nessus Vulnerability Scanner vs. OpenVAS
Nessus is often compared to OpenVAS. OpenVAS is an open-source vulnerability scanner created as a fork of the open-source code originally done for Nessus. Once Nessus started to be sold by Tenable Networks, then the Nessus fork of the code, named GNessUs, was later named as OpenVAS. The depth and breadth of vulnerability coverage in Nessus places it in an enviable position. Nessus may be aware of over 47,000 common vulnerabilities and exposures (CVEs) which is excellent coverage.
The positive recommendations on Nessus have included:
- Ease of use – this is facilitated by pre-built scripts.
- Nessus offers suggestions for remediation and mitigation of vulnerabilities found.
- Nessus is able to find many different vulnerabilities across many different platforms and operating system software.
- Nessus has also been praised for its reliability and ability to collate and assemble highly useful output.
- Nessus is said to have one of the lowest false positive rates and has the support of a commercial enterprise, so necessary to most enterprise users.
Get started with Bugcrowd
Hackers aren’t waiting, so why should you? See how Bugcrowd can quickly improve your security posture.