NIST Cybersecurity Framework
What is a cyber security framework?
Cybersecurity frameworks such as the ISO/ IEC 27001/27002 address business risk and help improve overall cyber defense. Adopting a framework provides structure and context around cybersecurity investments, and provides some assurance that industry best practices are met.
What is the NIST Cyber Security Framework?
NIST CSF (The National Institute of Standards and Technologies Cyber Security Framework ) is a set of standards to help companies improve their overall cybersecurity posture. The NIST CSF defines a set of best practices that enables IT organizations to more effectively manage cybersecurity risks. Organizations can voluntarily use this framework to assess their cyber risks and set plans for improving or maintaining their security posture over time. The framework focuses on using business drivers to guide cybersecurity activities and considering cybersecurity risks as part of the organization’s risk management processes. In addition, the framework provides a common taxonomy and structure for cybersecurity by assembling standards, guidelines, and practices that are working effectively today.
In August of 2023, NIST announced a 2.0 version of the framework will be released at the end of February 2024.
The NIST CSF framework consists of three main parts: the framework core, the implementation tiers, and the framework profiles. The framework core is a set of cybersecurity activities, outcomes, and informative references common across all sectors and critical infrastructure. Elements of the core provide detailed guidance for developing individual, organizational profiles. Framework profiles will help an organization align and prioritize its cybersecurity activities with its business objectives and requirements, risk tolerances, and resources. The tiers provide a mechanism for organizations to view and understand the characteristics of their approach to managing cybersecurity risk, which will help in prioritizing and achieving cybersecurity objectives.
The NIST CSF framework offers a flexible way to address cybersecurity. It applies to organizations relying on technology, whether their cybersecurity focuses primarily on information technology, industrial control systems, and connected devices more generally, including the Internet of Things. In addition, the framework can assist organizations in addressing cybersecurity as it affects the privacy of customers, employees, and other parties.
It is important to note that the NIST CSF framework is not a one-size-fits-all approach to managing cybersecurity risk for critical infrastructure. Organizations will have unique risks, including different threats, different environments, and different risk tolerance and will need to modify and customize the framework. Organizations can prioritize Investments to maximize the impact of each dollar spent. The goal of the framework is to reduce and better managing cybersecurity risks.
The NIST Framework Core
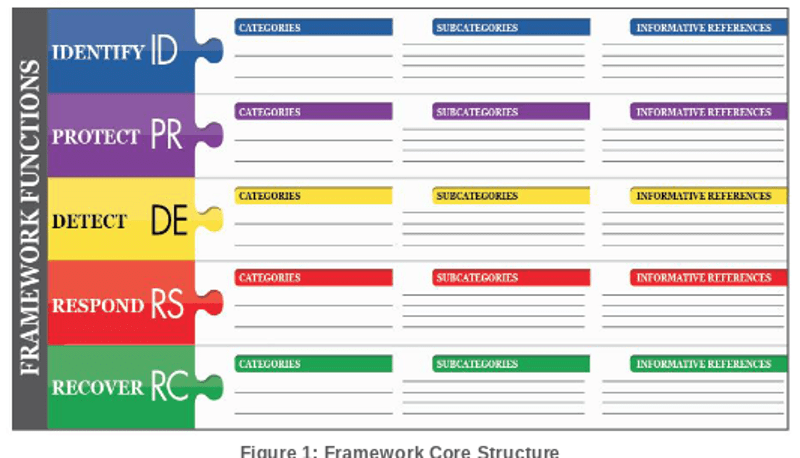
The framework core is a set of cybersecurity activities, desired outcomes, and relevant references common across critical infrastructure sectors. The core represents industry standards, guidelines, and practices that allow for communication of cybersecurity activities and outcomes across the organization from the executive level to the implementation/operations level. The NIST CSF framework consists of 5 concurrent and continuous functions. These include:
- Identify : Organizations manage cybersecurity risk to systems, people, assets, data, and capabilities.
- Protect : This function is where you develop and implement appropriate safeguards to ensure the delivery of critical protective services.
- Detect : This function is where you develop and implement appropriate activities to identify the occurrence of a cybersecurity event. The detect function enables the timely discovery of cybersecurity events.
- Respond : Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
- Recover : Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
When considered together these functions provide a high level, strategic view of the life cycle of an organization’s management of cybersecurity risk. The framework then identifies the key categories and subcategories which are discrete outcomes for each function. It then matches them with an example informative reference such as existing standards guidelines, and practices for each subcategory.
The NIST CSF Framework Implementation Tiers
The framework implementation tiers provide context on how an organization views cybersecurity risk and the processes in place to manage that risk. Tiers reflect a progression from informal reactive response to approaches that are agile and highly risky informed. During the tiers selection process, an organization should consider its current risk management practices, threat environment, legal and regulatory requirements, business and mission objectives and organizational constraints such as available budgets. The four tiers are:
Tier 1: Partial
- Risk Management Process : Not formalized and risk is managed ad hoc and sometimes reactive manner.
- Integrated Risk Management Program : Limited awareness of cybersecurity risk at an organizational level.
- External Participation : The organization does not understand its role in the larger ecosystem with respect to either its dependencies or dependents.
Tier 2: Risk Informed
- Risk Management Process : Risk management practices are approved by management but may not be established as organizational-wide policy.
- Integrated Risk Management Program : There is an awareness of cybersecurity risk at the organizational level, but an organization wide approach to managing this risk has not been established.
- External Participation : Generally, the organization understands its role in the larger ecosystem with respect to either its own dependencies or dependents, but not both.
Tier 3: Repeatable
- Risk Management Process : The organization’s risk management practices are formally approved and expressed as policy.
- Integrated Risk Management Program : There is an organization-wide approach to managing cybersecurity risk.
- External Participation : The organization understands its role, dependencies, and dependents in the larger ecosystem and may contribute to the community’s broader understanding of risks.
Tier 4: Adaptive
- Risk Management Process : The organization adapt its cybersecurity practices based on previous and current cybersecurity activities, including lessons learned and predictive indicators.
- Integrated Risk Management Program : There is an organization-wide approach to managing cybersecurity risk that uses risk-informed policies, processes, and procedures to address potential cybersecurity events.
- External Participation : The organization understands its role, dependencies, and dependents in the larger ecosystem and contributes to the community’s broader understanding of risks.
A Framework Profile
A framework profile represents the outcomes based on business needs that an organization is selected from the framework categories and subcategories. The profile can be characterized as the alignment of standards and practices to the framework core in a particular implementation scenario.
Profiles can be used to identify opportunities for improving cyber security posture by comparing a current profile with a target profile. A current profile defines the as is state, and a target profile defines the to be or desired state. To develop a profile, an organization can review all of the categories and subcategories, based on business and mission drivers in a risk assessment, determine which are most important. The current profile can then be used to support prioritization and measurement of progress towards the target profile, factoring in other business needs including cost-effectiveness and areas such as innovation. Profiles can be used to conduct self-assessments and communicate within an organization, or between organizations.
Comparison of profiles may reveal gaps to be addressed to meet cybersecurity risk management objectives. An action plan to address these gaps to fulfill a given category or subcategory can contribute to the roadmap described above. Prioritizing the mitigation of gaps is driven by the organization’s business needs and risk management process. This risk-based approach enables an organization to gauge the resources needed to achieve cybersecurity goals in a cost-effective, prioritized manner.
Assessing Cybersecurity Risk with the NIST CSF Framework
In summary, the cybersecurity risk framework is designed to reduce risk by improving the management of cybersecurity risk to organizational objectives. Ideally, organizations using the framework will be able to measure and assign values to the risk along with the cost and benefits of steps taken to reduce risk to acceptable levels. Organizations using the NIST CSF are better able to manage and measure its risk, expense, and benefits of different cybersecurity strategies. Over time, NIST CSF helps organizations develop a more rational, effective, approach to cybersecurity strategy and investment.
Get started with Bugcrowd
Hackers aren’t waiting, so why should you? See how Bugcrowd can quickly improve your security posture.