
Why crowdsourced security?
Most organizations lack the resources and diversified skills to find hidden vulnerabilities before attackers do. Unfortunately, using reactive tools alone leads to noisy, low-impact results that miss emerging risks. Even sophisticated companies can misjudge the creativity, patience, and diverse skills of today’s attackers.
Crowdsourcing emerged to address the skills gap—and the imbalance between attackers and defenders—by incentivizing ethical hackers to report critical bugs. Yet many firms struggle to integrate crowdsourcing into their security strategy in a trusted, efficient way; purpose-built tools are too limited, and consulting-based approaches fail to scale.
Bugcrowd has re-envisioned crowdsourced security with a SaaS platform that activates skilled, trusted hackers for your needs on demand, with all operational details fully managed for you at any scale.
Access expert talent
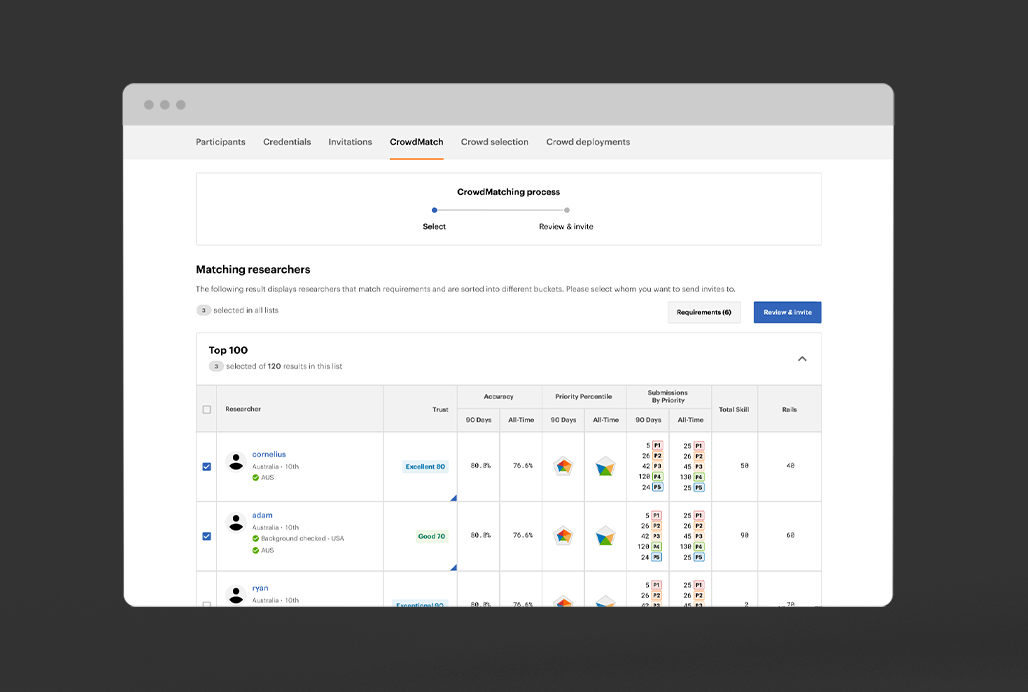
We curate and activate skilled hackers from a global, diverse community to bring the right crowd to your use cases at the right time.
Go beyond bug bounty
Bug Bounty is just a start. Bugcrowd Penetration Testing as a Service, for example, is enhanced by crowdsourcing in numerous ways.
Get a platform advantage
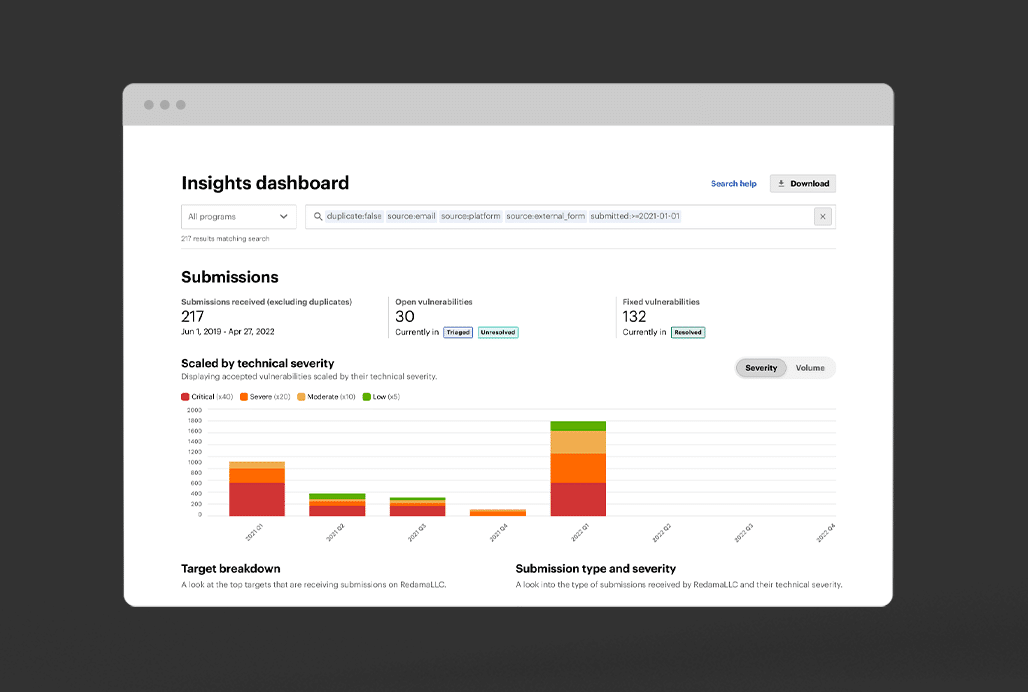
The Bugcrowd Platform enables the scale, consistency, and continuous improvement that siloed tools and consulting can’t deliver.
Build on past success
Only our platform captures a decade of accumulated crowdsourced knowledge about vulns, assets, hacker skills, and environments.
Trust in triage
Successful crowdsourcing depends on rapid, battle-tested triage and prioritization so you reduce the noise and remediate faster.
Use data, tech, and humans
Effective crowdsourcing depends on the orchestration of data, technology, and human intelligence to speed vulnerability remediation.
How it works
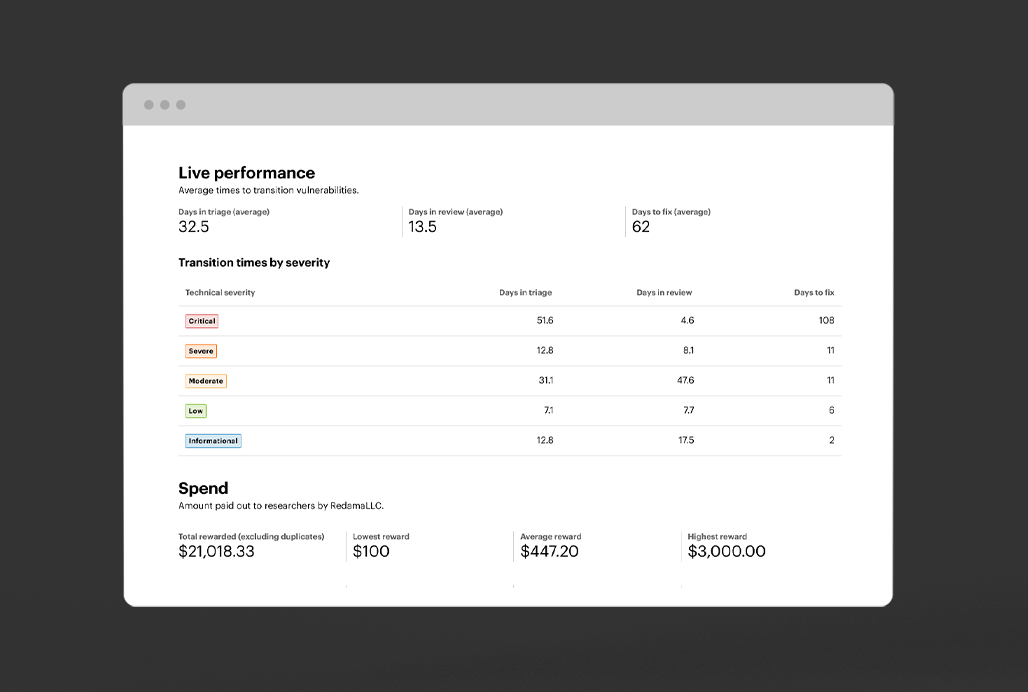
Trusted by the best
Use cases
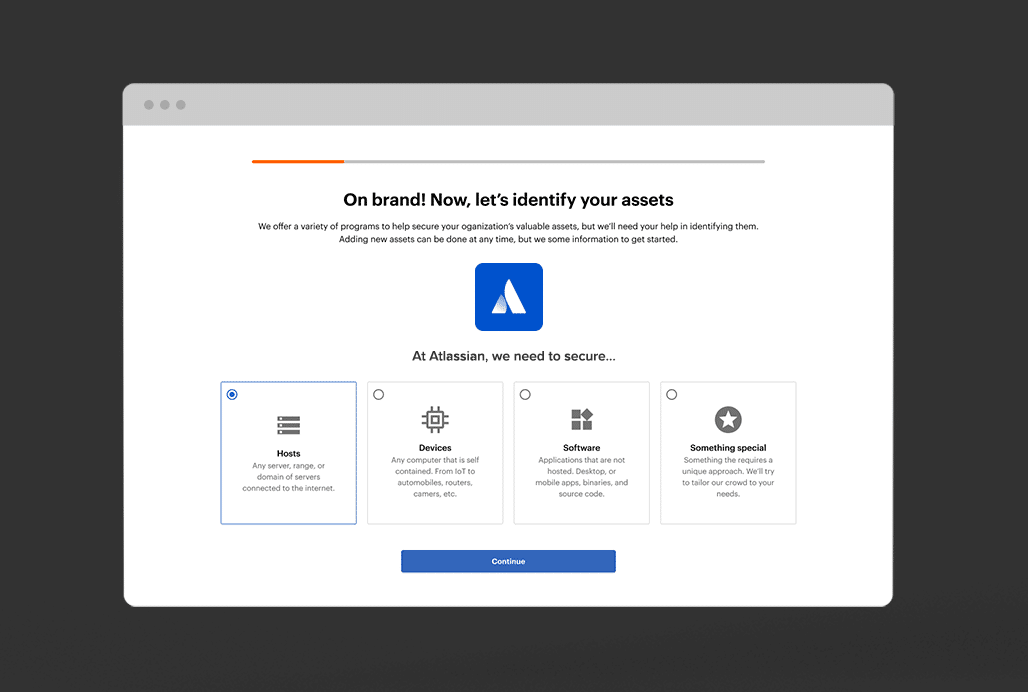
Which assets can benefit?
Crowdsourcing has benefits for many asset types, both internal and external. There are no agents, clients, appliances/devices to install or manage. Plus, with our fully managed solutions, operational overhead is minimal.
-
Web Apps (Cloud and On Premises)
-
APIs
-
Networks
-
Cloud Services
-
Mobile Apps
-
loT
-
Social Pen Test
Get started with Bugcrowd
Hackers aren’t waiting, so why should you? See how Bugcrowd can quickly improve your security posture.