
Maintaining Program Success & Being an Effective Program Owner
By Grant McCracken, April 4, 2019
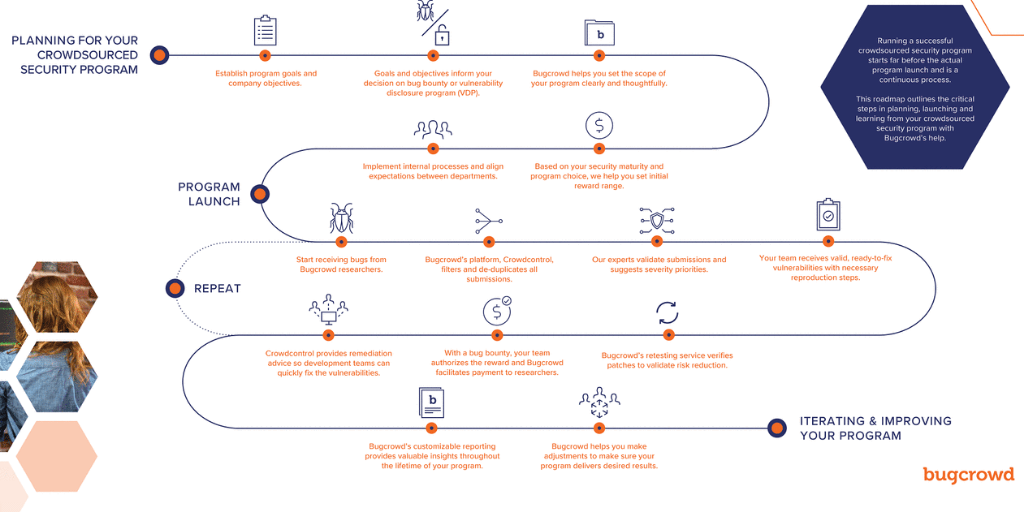
Process For Launching Your Crowdsourced Security Program
By Grant McCracken, March 20, 2019

Managing Your Crowdsourced Security Program for Success
By Grant McCracken, March 7, 2019
5 Tips and Tricks for Running a Successful Bug Bounty Engagement
By Grant McCracken, October 2, 2018

Providing Access to your Program: Sharing Isn’t Caring
By Grant McCracken, December 12, 2016
All You Need to Know About Bug Bounty Testing Environments
By Grant McCracken, October 12, 2016

Essential to a Successful Bounty Brief: Exclusions
By Grant McCracken, June 29, 2016

How to Write a Clear and Thoughtful Scope, A Deep Dive
By Grant McCracken, May 2, 2016
Subscribe for updates
Get Started with Bugcrowd
Hackers aren’t waiting, so why should you? See how Bugcrowd can quickly improve your security posture.

