Bugcrowd has reported on the state of bug bounties since 2015, analyzing data from vulnerabilities submitted through the Crowdcontrol platform and on the Crowd itself. This year, we introduced the inaugural 2019 Priority One Report, expanding the scope of our analysis into the state of crowdsourced security (Vulnerability Disclosure, Bug Bounty, and Next Gen Pen Test Programs), and focusing in on the most critical bugs uncovered over the last year.
Critical Bugs
The number of security vulnerabilities reported and bug bounty payouts per vulnerability nearly doubled this year compared to last. But even more, there was a major shift in vulnerability classes found by security researchers in 2018. Looking back to 2017, nearly nine in 10 of the critical and high vulnerabilities found were classes that we’ve traditionally seen year in and year out.
In 2018, the focus shifted away from easier-to-find bugs and low-hanging fruit. Four-out-of-five of the top Vulnerability Rating Taxonomy (VRT) classes revolved around vulnerabilities that are difficult, if not impossible, for any machine to find:
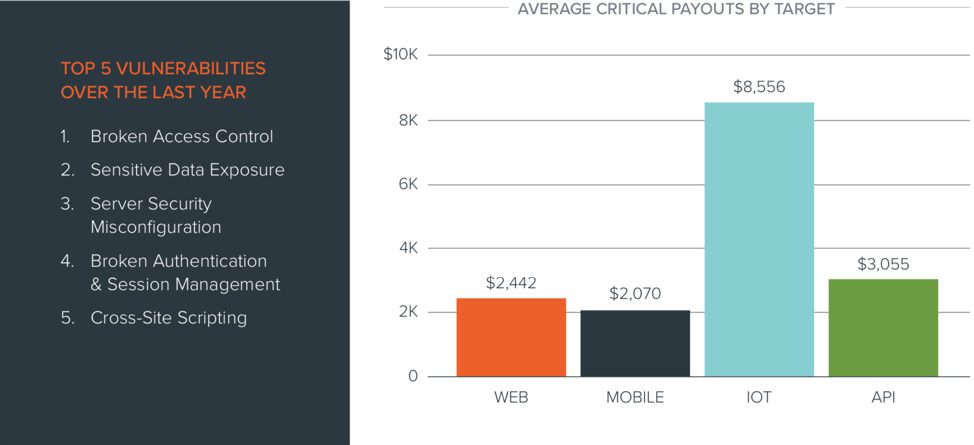
- Broken Access Controls
- Sensitive Data Exposure
- Server Security Misconfiguration
- Broken Authentication & Session Management.
These are systemic issues with critical impact, and there are very few programming frameworks out there that protect against them. The ones that do are far from perfect.
This major shift is signaling a new era of deep testing like we’ve never seen before. Many organizations out there today have employed scanners, and the like, to protect against easy-to-find, low-hanging fruit. But where do you go from there once all of that automation is set up? Organizations must look past traditional methods of security testing, instead adopting a layered approach where human creativity is the added solution for deep testing.
Since the State of Bug Bounty Report in 2015, Bugcrowd’s Crowd has grown more than 10X. We bring together the creativity of hundreds of thousands of trusted hackers from all around the world, and provide the platform to match their skills to the right project. It’s no wonder they’re uncovering more and more critical bugs. And there are payouts from the market to match — the average payout for a critical vulnerability has reached nearly $2,700 this year!
Average Critical Payouts by Target
One thing that hasn’t changed in our latest report is the prevalence of web vulnerabilities, which are still on the rise. It’s no surprise since the web is still the largest attack surface out there, and accounts for 90% of all submissions through our platform. While this trend will continue over the next year, these vulnerabilities might come in different flavors as widespread migration to the cloud and connected devices continue to surge.
In fact, we saw a nearly 4x increase in vulnerability submissions for IoT targets, with average payouts surpassing $8,500. Why?
The current state of IoT security is a serious threat to businesses. Gartner predicts there will be 25 billion IoT devices in the world by 2021, yet most devices have gone largely unregulated and unsecured. The sheer number and types of the devices being networked and connected to cloud interfaces and on-the-internet APIs is one of the greatest challenges in security today. Each device has its own set of technologies, thus introduces its own set of security challenges.
To read more on IoT security, check out the IoT Security Spotlight Report.
Looking Ahead
New technology environments are going to require more skills and education to combat the new vulnerabilities that will appear alongside. Crowdsourced security has already quickly proven return in keeping pace with the growing attack vectors.
We saw evidence of this in the case of Equifax, where Bugcrowd hackers found and fixed the same vulnerability that compromised Equifax in a similar institution a full four months before the breach occurred — saving them the nearly $1.4 billion that Equifax spent on cleanup costs.
To learn more about the most critical bugs of the year, and how to stay secure, download the full Priority One Report here.
Be sure to also register for our upcoming webinar on going from “Oh Sh*T to Fixed” on Thursday, August 29 at 10am PT. Bugcrowd CSO David Baker will discuss best practices for closing the feedback loop once the Crowd has helped you to uncover a critical bug.