Last week, some 36,000 professionals from around the world came together for RSA Conference 2020 to sanitize their hands identify business opportunities and share their vision of a safer tomorrow. This year’s theme, Human Element, sharpened the corporate lens to reveal the front lines are responsible for more than just securing data—they safeguard every facet of the digitally-connected world and protect some of the most vulnerable people. In this blog, we’ll recap critical themes from the expo hall, and share thought leadership from both hackers and security engineers.
Attackers are more equipped and motivated than ever, which seemingly fuelled the passion vendors brought with their employees sharing security expertise through keynotes, booth presentations, and the occasional “I just wanted a fidget spinner” swag-for-a-scan sales pitch (RIP). This zeal was made apparent by a marked shift towards edgier messaging in the expo hall. For example, Malwarebytes creatively described itself as a means to “Keep business productive af,” while Axonius offered a comical concession that “Asset management isn’t sexy.” Similarly, landmark security veteran, Check Point, activated the encompassing brand promise “Secure your everything” (which is fine…unless there’s nothing left to secure because you used Zscaler to “Eliminate your attack surface.”)
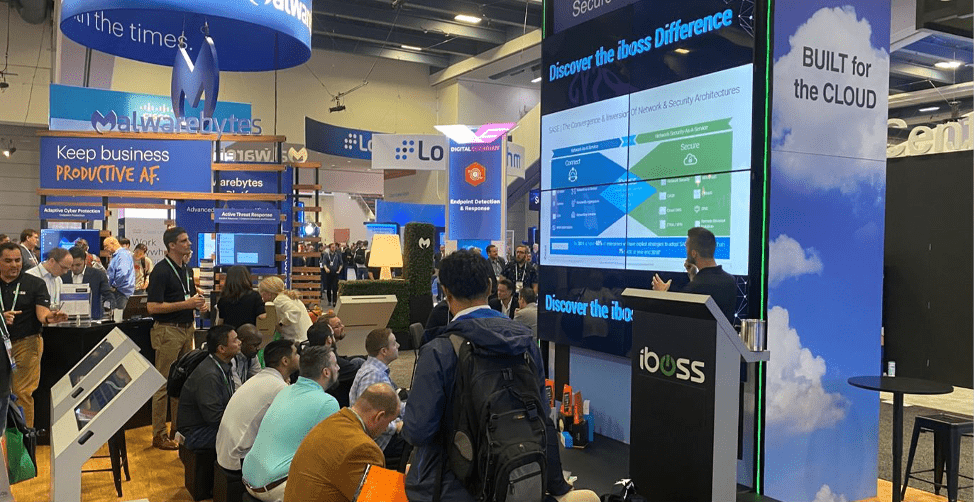
Key themes from the expo hall
Three specific topics permeated the show floor—here’s what you need to know about them:
-
- Security Personification
The most pervasive theme, by far, was concerned with the “intelligence” of security. Many products described themselves broadly as “intelligent security” or “smarter security,” and sometimes even blended the attributes to form personified propositions. While these technologies may help to remediate risk, the truth is that inanimate security products don’t miraculously become smarter: the people who build them do. What you need to know is that intelligence isn’t a feature—it’s the benefit of having had the right humans solve a specific set of problems.
-
- Cloudpocalypse
It’s safe to say that 2020 will go down as the year the industry began coming to terms with jumping into the cloud head first. We’re now ten years into the modern cloud (can you believe it’s older than the first iPad?!), and vendors surfed the metaphor’s third wave with elaborations like “multi-cloud world” and “cloud-enabled threats.” What you need to know is that the cloud isn’t as soft or fluffy as the advertisements made it out to be—it’s a myriad of different challenges that continue to demand specific expertise with unprecedented scale.
-
- The Same But Different
Language in the expo hall was colored in strokes of modernity and futurism, with many vendors proposing a “new approach” and offering “security reimagined.” Some even pressed organizations to “reimagine their perimeter,” while others claimed that contemporary cybersecurity now operates in a “post-perimeter world.” What you need to know is that however you conceptualize your attack surface and threat landscape, there’s nothing modern about solving complex security problems in novel ways—it’s something we’ve been helping world-class brands like Mastercard, Atlassian, and Motorola do for years.
Taking over Local Edition and DNA Lounge
For two days, Bugcrowd transformed Local Edition into an underground oasis where attendees could enjoy barista-made coffee, rolling appetizers, and any charger cord they could possibly need. Guests also had the opportunity to rub shoulders with infosec leaders and hear diverse perspectives on a variety of evolving problems.
Here’s a recap of speaker sessions held live at Local Edition:
Builders vs. Breakers
In this fireside panel, guests learned how to make sense of their threat landscape through the eyes of a hacker. Grant McCracken, (Sr. Director of Security Operations), Michael Skelton (Top-50 Security Researcher and Global Head of Security Operations), and Leif Dreizler (Sr. AppSec Engineer at Segment) joined forces to explore how organizations can leverage the power of crowdsourced security to secure their assets proactively. Speakers advocated distinct perspectives from the researcher community and security teams, and discussed how they work together best to find more critical vulnerabilities.
Our #RSAC “Builders and Breakers” event is starting! Introducing our panel:
Grant McCracken, Sr. Director of Security Operations at #Bugcrowd
@codingo_, Global Head of Security Operations at #Bugcrowd
@leifdreizler, Sr. AppSec Engineer at @Segment pic.twitter.com/HdQVBtmvw1— bugcrowd (@Bugcrowd) February 25, 2020
5 Ways You Can’t Fake the Human Element
In this session, Michael Skelton (aka Codingo) explained the one problem with cybersecurity racing towards a future of automation: technology still can’t outwit the human creativity of a hacker. He discussed why the enterprise has become increasingly reliant on data, and how hackers use a variety of methods to enter their systems undetected to extract valuable information. Skelton also shared 5 ways that scanners can’t catch the same vulnerabilities as humans, and gave insight on how he went from hacking by the beaches of Australia to becoming Global Head of Security Operations at Bugcrowd.
Listening to @codingo_ talk about 5 ways you can’t fake the human element at @Bugcrowd’s session at @LocalEditionSf! #RSAC2020 pic.twitter.com/jHdHCKFO8Z
— Don McKenzie (@TheDonMcKenzie) February 26, 2020
You may have also spotted Bugcrowd around San Francisco as our “said no one in security” campaign hit newsracks across the city:
Tell us your worst case scenarios and fill in the blank
______________, said no #CISO ever.#saidnoCISOever #RSAC pic.twitter.com/gvhVwiSflO
— bugcrowd (@Bugcrowd) February 25, 2020
Now, RSA Conference wouldn’t be quite the same without Bugcrowd’s 4th annual afterparty. This year, we kicked it up a notch with a change of venue that put music and entertainment at the heart of our event. Headlined by the synth-wave band, The Midnight, DNA Lounge was transformed into an after-dark experience that resembled something you might see in a Tank Girl comic. Guests didn’t just battle on the dance floor. In essence, they also battled each other playing retro arcade games, choosing where to get an airbrush tattoo, and seeing how many different pairs of novelty sunglasses a single person could wear in the photo booth (busted!).
The party is just getting started at @dnalounge #mayhem2020 pic.twitter.com/oqhzsvZMeP
— bugcrowd (@Bugcrowd) February 27, 2020
Check out photos from the event and download your personal keepsake here.
Looking Ahead
RSA Conference remains a signature event for many of the largest enterprises, helping the industry mature while preparing professionals to face their next challenge. One thing is clear: organizations must balance the Human Element with new efficiencies and scale afforded by technology to be successful. That’s why Bugcrowd has invested significantly in expanding our technology stack to integrate collective creativity at every stage of the security development lifecycle—for faster access to the skills that matter most—wherever and whenever you need them.
If you missed us during the show, you can still request a meeting or check out DarkReading’s coverage of new enterprise enhancements made by Bugcrowd, enabling organizations to access a wider range of security skills with more relevant experience to their unique security concerns. These enhancements include:
- Increased visibility: users of Attack Surface Management report up to a 97% reduction in unknown attack surface.
- Increased control: more oversight over multiple programs and the ability to spin up on-demand programs through a simple wizard which defaults to proven Bugcrowd best practices.
- Increased access: CrowdMatch™ democratizes access to researchers with the best skills to help enterprises find high-impact vulnerabilities first and provide contextual intelligence so they can fix faster. Industries like FinServ, Telecommunications, and IoT, report their first critical submission in under 1.6 days on average.
DarkReading also explained how Bugcrowd is helping CISOs better manage budgets and maximize impact from programs with two new in-platform reports:
- Security Posture report: identifies the vulnerabilities within an organization’s technology stack against industry benchmarks and prioritize areas of improvement.
- Health and Spend report: captures program performance and spending patterns as well as context-aware recommendations for program improvements.
For more product updates, be sure to read our latest blog on how Bugcrowd is accelerating security success with auto-join programs, enhanced skill matching, and new API extensions.
You can catch Bugcrowd next at these upcoming events:
- Nullcon: March 3-5, 2020
- SecureWorld Boston: March 25-26
- FS-ISAC Spring Summit: May 17-20, 2020
- BSides London: June 3, 2020
P.S. Bugcrowd was also proud to be the official Brown M&M sponsor for @wendynather:
#RSACprep WHAT THE ACTUAL I SAID NO BROWN M&MS pic.twitter.com/qfO9Yh8P1A
— (@wendynather) February 25, 2020



