Earlier this year, we took a closer look at why every company should have a vulnerability disclosure program.
As veterans with combined 40+ years in the cybersecurity space, Bugcrowd founder and CTO Casey Ellis and CSO David Baker each gave unique perspectives on the challenges of being a CISO today, how crowdsourced security can strengthen your security posture, and how vulnerability disclosure programs fit into a cohesive security program.
What every CISO is facing
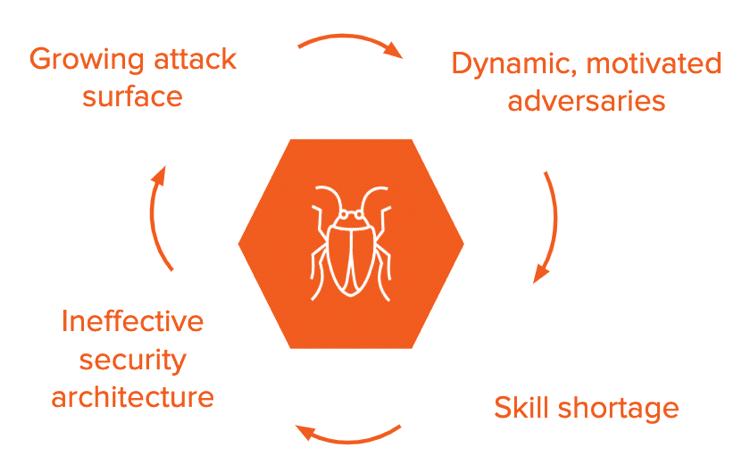
Figure 1: Problems every CISO is facing
Cybersecurity has never been simple or easy. But as attacks continue to evolve, attackers become more inventive, and the cyber skills gap widens, how do we help CISOs address all the challenges they face, while considering operational and budgetary restraints?
As a CISO, you’re forced to balance proactive security investments with the resources and processes needed to also react quickly when needed. As a security professional, you’ll need to learn how to operate within the context of both, and that includes learning how to work with outsourced teams, such as is the case with crowdsourced security solutions.
Gartner predicts worldwide InfoSec spending to exceed $124 billion this year alone, and $170.4 billion by 2022. Organizations are starting to recognize that malware is a publicly available commodity that makes it easy for anyone to become adversarially motivated. On the other end, more and more companies are offering brittle security solutions that do little to defend against attacks.
Enter crowdsourced security and VDPs
With motivated attackers and the proliferation of data breaches, CISOs today need to meet scale with scale — a crowd to match the world of bad actors. Crowdsourced security offers a clear solution, harnessing a global community of whitehat hackers to find and eliminate vulnerabilities through public or privately managed programs.
With the large supply of whitehat hackers underutilized, Bugcrowd exists to connect the collective creativity of the Crowd to scale security for CISOs and their organizations. One of the easiest ways to do so is through a vulnerability disclosure program, which offers a secure channel for researchers to report security issues and vulnerabilities, and typically includes a framework for intake, triage, and workflows for remediation. Think of it like a “neighborhood watch” for your internet assets.
Major companies like Walmart, Office Depot, and Motorola Mobility actively use vulnerability disclosure programs to provide a submission channel to the wider researcher community.
Why do organizations adopt VDP?
Although every vulnerability disclosure program is different, and should be tailored to the specific threat profile of your enterprise, there are three main drivers to the VDP adoption wave.
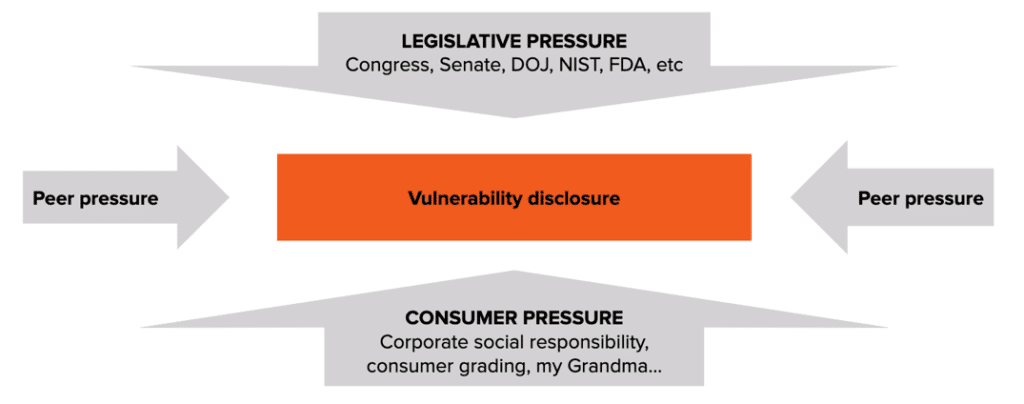
Figure 2: Pressures to adopt VDP
Legislative Pressure
Standardization is being applied to VDPs by major legislative bodies, with definitions published by the U.S. Department of Justice (DoJ) and in ISO 29147. In Europe, VDPs are being used to comply with GDPR.
The Center for European Policy Studies also recently stated that VDPs may reduce the risk of incurring fines arising from possible personal data breaches. This might suggest that, in the case of a GDPR-related breach, the absence of a VDP could be seen as worthy of penalization.
Protecting your brand and listening to your customers
A vulnerability disclosure program is an essential tool in a layered cybersecurity approach. By opening this channel to an army of whitehats, organizations not only demonstrate their commitment to protecting their digital assets and customers, but also respond and remediate known risks faster.
Not only does a VDP open a communication channel to external researchers, but also to current customers using your product to participate in the feedback loop. While CSO at Okta, Baker realized having a vulnerability disclosure program was an important part of rounding out his security program to intake vulnerabilities not only from researchers, but also from customers using the product. This was essential in strengthening Okta’s security posture.
Formalized security feedback
Security is an inherently messy process — it’s about preparing for events that aren’t supposed to happen in the first place. With sometimes conflicting goals, such as getting products to market quickly, you can’t expect perfection from your engineers and security team. However, you can minimize your risk by scaling your ability to protect your broader organization with a vulnerability disclosure program.
Having a vulnerability disclosure program in place also provides a better solution to the often latently managed @security mailers or “contact us” forms. Embedded security forms like those provided by Bugcrowd ensure you’ll get the information you need to action every vulnerability quickly, without excessive back and forth. And with a fully managed service, you can be confident that the right teams will get that information without delay.
Vulnerability disclosure programs with Bugcrowd
Bugcrowd’s fully-managed vulnerability disclosure programs provide a framework to securely accept, triage, and rapidly remediate vulnerabilities submitted from the global security community, all from our all-in-one SaaS platform, Crowdcontrol.
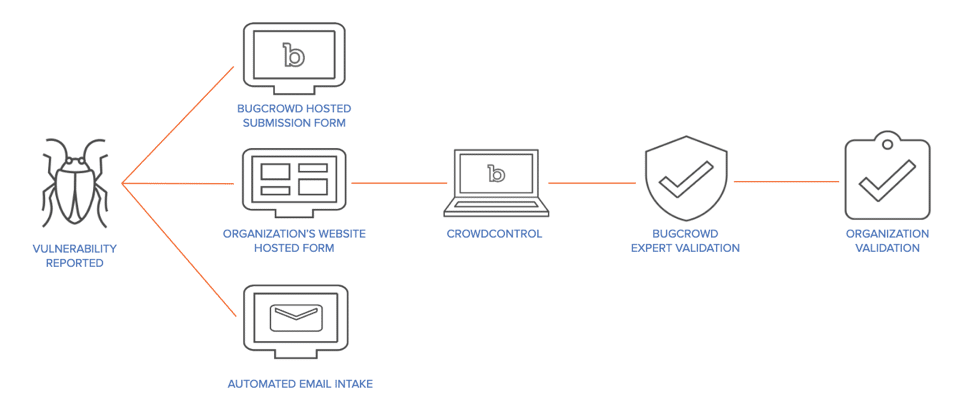
Figure 3: VDP with Bugcrowd
Crowdcontrol, combined with our in-house team of security experts, facilitates hundreds of managed vulnerability disclosure programs, escalating high-priority issues within hours and averaging triage completion within one business day. All the vulnerabilities coming through the researcher crowd are first vetted by Bugcrowd, according to objective rating standards like our own Vulnerability Rating Taxonomy (VRT).
Bugcrowd removes virtually all overhead for your security team so they can focus on reducing risk by remediating the vulnerabilities identified — making your security team happy and efficient.
To learn more about the additional benefits of a VDP, catch the full webinar here.




