Find and fix common issues fast
Identify common vulns like weak credentials, insecure networks, interfaces, device management, and lax data storage.
Tackle complex devices with equal ease
Testing requirements for devices and hardware can be extremely diverse, so IoT pen tests can be modified to suit individual testing needs.
Rely on battle-tested standards
Our methodology follows common testing standards such as OWASP, PTES and OSSTMM.
Use the right pentesters and tools for the task
We combine human-driven testing by a curated team of experts, scanners, and custom tooling to get the high-impact results you want.
Curated Pentester Teams
Use a team your assets deserve
Other pen test providers rely on a cookie-cutter approach regardless of your specific assets, environment, or needs–virtually guaranteeing low-impact results. Instead, we use the power of CrowdMatchTM AI in our platform to curate qualified, motivated pentester teams for your precise requirements, boosting high-quality results over other methods.
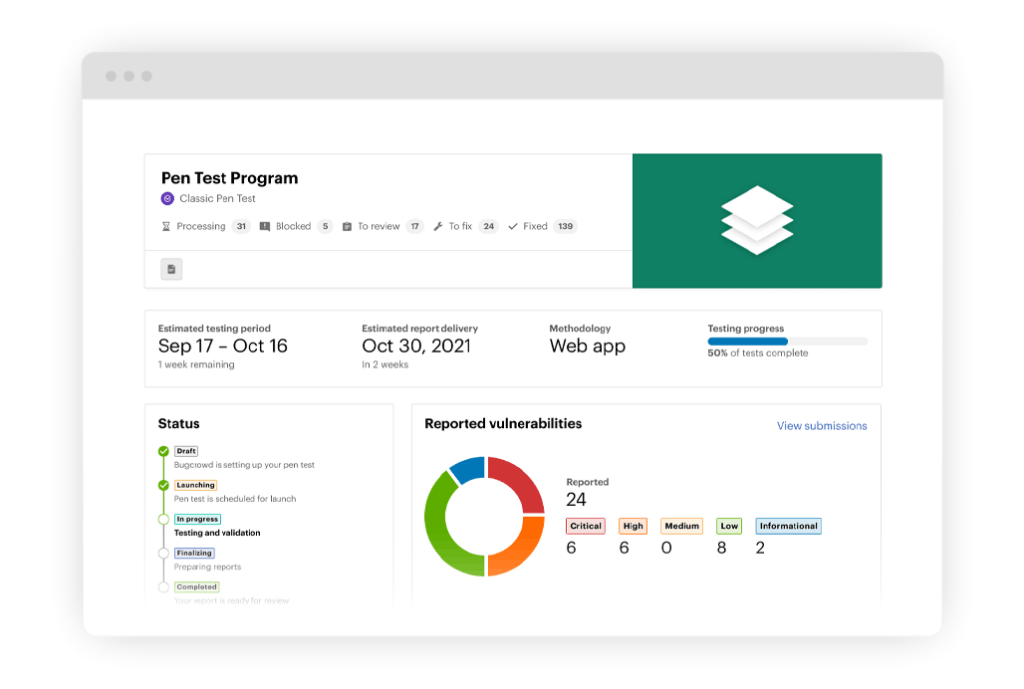
Penetration Test Dashboard
See results as they happen
Never be in the dark about your pen test results again. You can view prioritized findings, action items, analytics, and pentester progress 24/7 through the methodology checklist in a rich dashboard designed specifically for pen testing workflows. When ready, your final report (see sample) is available for download from the same dashboard.
Pen Test Products
Optimized for today’s most demanding cybersecurity requirements
A Pen Test Offering for Everyone
Includes:
- Basic report
Includes:
- Standard report
- Expert, trusted pentesters (CrowdMatch)
- Real-time Pen Test Dashboard
- Integration with SDLC
PLUS
Web Apps, Networks, Mobile Apps, APIs, Cloud Services, IoT
Everything in Standard +
- Detailed report (e.g, can be customized for specific regulations)
- Support for special pentester requirements: Geolocation restrictions, special skill sets, etc.
- Access to Solution Architect
- Retesting
- Internal Targets
MAX
Web Apps, Networks, Mobile Apps, APIs, Cloud Services, IoT
Everything in Plus +
- Choice of continuous or time-boxed testing
- Methodology-driven pen test combined with incentivized bug bounty
Speed & Scale
Launch tests in days, not weeks. Findings flow directly into your dev and security processes for rapid remediation.
High-impact results
Meet compliance goals and surpass them when needed by incentivizing pentesters for results. (See Sample Report)
Deep configurability
Count on a pentester team built for your precise needs. Mix and match test types, methodologies, durations, and models.
Real-time visibility
View findings and pentester progress through the methodology checklist in real time via the Bugcrowd Platform’s rich Penetration Test Dashboard.






Get started with Bugcrowd
Attackers aren’t waiting, so why should you? See how Bugcrowd can quickly improve your security posture.


