If the last 18 months have taught us anything about cybersecurity, it’s that moving work environments and software supply chains to the cloud has attackers proverbially gunning their engines. Attack vectors like ransomware and N-day attacks are causing security leaders to respond quickly and more creatively to the all-too-common risk of being blindsided by surprises like the recent Log4j incidents, as reactive tools can only help you address vulnerabilities that you already know, not the ones you don’t.
The Enterprise Strategy Group has found that the average organization’s attack surface is 40% “unknown”–and that was before the pandemic created a long tail of security debt from hastily built hybrid work environments on vulnerable or misconfigured cloud services. Researchers at Palo Alto Networks recently found that after setting 320 honeypot nodes comprising common tools — SSH, Samba, Postgres, and RDP — across public cloud infrastructure, 80% of those nodes were compromised within 24 hours, and all of them were compromised within one week.
The uptake of cloud data warehouses and cloud data lakes, adoption of cloud-native web applications using containers and microservices, and reliance on new identities, tokens, and APIs–all staples of the modern software supply chain powering digital transformation, and many based on open source code–expand and complicate the attack surface exponentially. (APIs are particularly vulnerable; per Gartner, by 2022, 90% of cloud apps will be more vulnerable to attacks through APIs than human-facing UI.) CISOs and corporate boards get grim reminders of this material risk over and over, with Log4j and its Log4Shell exploit being just the latest example.
Augmenting Automation
In some organizations, automated tools have been thought to be the sole answer, especially given the chronic shortage of cybersecurity professionals. However, automation is no silver bullet; attackers have access to the same tools and supplement them with domain knowledge, creativity, and intuition. They can uncover new vulnerabilities before scanners do because automation can only help detect risks that have already been observed in the wild–and when they do, the results are incredibly noisy and may not be comprehensive. (The Log4j vuln is an example that, due to deep inter-dependencies, can easily evade scanners.) New, previously unseen vulnerabilities types, many of them critical, appear at the same rapid pace that new cloud applications are written, evading automated tools until they can adapt to those new risks.
Instead, cloud security requires the augmentation of the existing ecosystem of automated tools with a proactive, platform-powered approach that has these key characteristics:
- Persisted knowledge about vulnerabilities, assets, targets, and environments to bring contextual intelligence to your security operations–for example, to understand which assets are most at risk based on similar environments and/or known vulnerabilities, or for benchmarking your results against the industry
- Automated workflows that integrate with existing DevOps processes to ensure apps and APIs are continuously tested before they ship
- A deep investment in human intelligence, such as the ability to collaborate with precisely the right skilled, trusted security researchers (the crowd) on demand for bleeding-edge hacker skills, because only anticipating the attacker mindset can help you find critical hidden vulnerabilities as they emerge. Rapid validation and triage, enabled and informed by the knowledge and automated workflows described above, are critical to make those results actionable.
The Bugcrowd Security Knowledge Platform uniquely orchestrates all of the above to defend against blindside cloud security attacks with proactive solutions spanning Penetration Testing-as-a-Service, Vulnerability Disclosure, Bug Bounty, and Attack Surface Management. For example, traditional, time-bound penetration testing approaches are not built to address the rapid pace and agility common to cloud services and cloud-native applications. Continuous pen testing-as-a-service, augmented by an incentivized crowd, offers a more comprehensive approach compared to running annual/infrequent pen tests. Bugcrowd cloud pen tests can be deployed against AWS, Azure, Google Cloud, and virtually any other environment to find ~70% more vulnerabilities than you would find using other methods, per IDC.
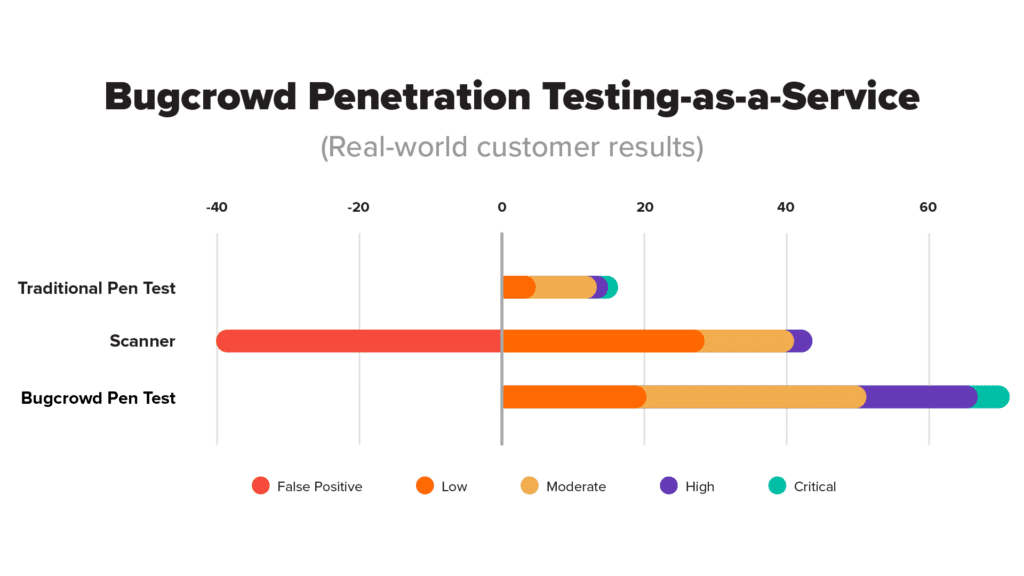
Complementing pen testing as a service with other solutions (see below) provides the broad, deep coverage that defends against blindside cloud application attacks:
- Attack Surface Management: Cloud services are easy to procure, and can be highly elastic and transient. Continuous visibility into your cloud services attack surface–augmented by a crowd of researchers specifically curated for your needs to add much more coverage than automated scanning–is critical to avoid an unknown asset or misconfigured service from being used in an attack.
- Vulnerability Disclosure: Hackers and even casual users can stumble upon potential vulnerabilities in your cloud applications. Not having a standardized, coordinated way to receive and handle reports about potential vulnerabilities is a serious risk for your products and your reputation. Our 2021 Inside the Mind of a Hacker research found that 58% of ethical hackers won’t bother to report a vulnerability if there is no clear process for disclosing it.
- Bug Bounty: Cloud environments are complex. When outside of pen testing cycles, incentivizing discovery of hidden critical bugs by a curated crowd matched precisely to your needs and environment is crucial for identifying emerging risks that automated or reactive tools won’t find.
Go Beyond
Cloud application security requires an approach that goes beyond the status quo, and certainly beyond checkbox compliance–the risk of doing anything else is far too high. Learn more about how the Bugcrowd Security Knowledge Platform uniquely addresses that risk here.



