Penetration testing is a key cybersecurity best practice. Most organizations understand the need for it, but like many things in the industry, penetration testing can be a bit confusing. This blog covers penetration testing 101, helping to uncover the basics, explain the importance of penetration testing, show you how to perform these tests, dive into the different types of tests, and help you determine which test is right for you.
What is Penetration Testing?
For those dipping their toes into the world of penetration testing, penetration testing is the process of hacking into your own system and network to identify and expose as many vulnerabilities as you possibly can, from multiple vantage points.
But wait, isn’t hacking a bad thing? We live in a world where the word “hacker” conjures up images of men in dark hoodies in front of a laptop in their parents’ basement. That stereotype is completely inaccurate. Hackers come in all shapes and sizes, and many have altruistic motivations.
Penetration testing is performed by “ethical hackers” or security researchers who are highly specialized. Penetration testers search for vulnerabilities with full knowledge and authorization from the client. When protecting your organization from malicious hackers, you want to think like one so as to anticipate and protect where they might strike your organization. And what better way to think like a hacker than to have an ethical hacker as part of your security team?
Let’s take a step back for a quick history lesson. Penetration testing, which started in the ‘90s as adversary simulation, was never meant to find every security flaw. Its goal was to identify vulnerabilities that a malicious actor would likely be able to exploit. It was quickly adopted as a security best practice and as a compliance initiative, designed to assure regulators and other stakeholders that an organization takes security measures seriously.
In the late 2000s, the industry saw an explosion in vulnerability scanners and scanner-assisted services. This seemed like the perfect solution due to strained resources. However, as we’ve learned in the security world time and time again, machines alone never hold up to human ingenuity. Even the most advanced scanners of today are unable to detect many of the vulnerabilities that humans can.
Why is Penetration Testing Important?
Penetration testing is a mainstay in cybersecurity for several reasons. It is most commonly used to protect the organization and its assets, but it has a lot of other benefits as well. The top five reasons why penetration testing is important are:
- Protecting the organization and its assets from cyber attacks
- Protecting customer data
- Reducing cyber risk
- Satisfying stakeholder and compliance requirements
- Preserving the organization’s image and reputation
The fifth reason is especially interesting as it is an emerging priority. During an era of high-profile security breaches reported on the news such as Target, Equifax, and Marriott, even the least tech-savvy person can understand the importance of cybersecurity. We now live in a world where everybody has security in the back of their mind each time they swipe a credit card or input personal information online.
When discussing the importance of penetration testing, we’d be remiss if we didn’t mention compliance as a factor. Several rigorous compliance standards exist, such as The PCI Data Security Standard v3.2.1, NIST 800-53 revision 4, ISO:IEC 28001 Annex A, and Cybersecurity Maturity Model Certification CA.4.164. While only 16% of organizations test purely for compliance sake, 55% of organizations cite compliance as one of their reasons for testing.
How Are Penetration Tests Performed?
There are several steps in the penetration testing process. Not all firms include each step, but in a good, crowdsourced process, you can expect these 13 stages:
- Scoping
- Information gathering/planning
- Pen tester matching
- Reconnaissance/discovery/scanning
- Vulnerability discovery and assessment
- Continuous analysis and review of findings
- Consolidation of findings for a final report
- Integration into SDLC for routing findings to development teams
- Remediation of findings and acceptance of risk for non-remediation
- Retesting of fixed vulnerabilities
- Exploitation
- Analysis, reporting, and review
- Clean up/tear down
There are generally four different ways of performing a penetration test. The first method is internal testing, which simulates the damage that employees could unknowingly make on your systems. The second method is external testing, which simulates the damage outside attacks could make on your visible DNS, web servers, email servers, and firewalls. Blind testing is a method that simulates how attackers get company information and attack, all without prior information before attacking. The final method, double-blind testing, simulates a real attack, meaning no information is given to the penetration tester and no notice is given widely within the organization.
Pentesting Methodologies
Once you decide on the method that is best for your organization, you also need to educate yourself on the different methodologies that vary by target type, compliance initiative, and more. Here are the four primary ways for deploying services:
- Traditional Penetration Testing – This model comprises one or two testers working against a set methodology for a defined period, usually anywhere from three days to two weeks. Some pros of this method include it being an established budget line item, a known quantity, and best suited to targets that require physical presence to access/test. On the other hand, it is known to have delays in scheduling and results, to be inflexible with questionable skill fits, and not optimized to incentivize true risk reduction.
- Crowdsourced Security Penetration Testing – This model, although comparatively new, is rapidly growing, utilizing a large pool of remote, pay-per-project testers. Often combined with an incentivized ‘pay for results’ approach to billing, crowdsourced testing is quickly becoming the top choice for organizations seeking more from their security testing services. Crowdsourced pentesting offers a rapid setup and time to value, real-time results, and SDLC integration. However, it is not optimized for highly sensitive or physical targets too big to ship and the ‘bounty’ approach may not fit buying cycles.
- Internal Security Team – While often not feasible for smaller organizations, some enterprises prefer to build and maintain in-house teams of security testers. This approach allows the organization to maintain full control, setting its own testing schedule. This approach is best for extremely sensitive work, with little marginal cost to testing. Negatives to this approach include it being fairly labor-intensive to set up and maintain and it leaves organizations unable to retain all possible testing skills or to acquire new skills when needed.
- A Mixed Testing Approach – This is a combination of the above three methods to meet the specific needs of each project. This approach includes the best and worst aspects of each method, with the potential for thorough security coverage, but also a high cost and complex setup to maintain.
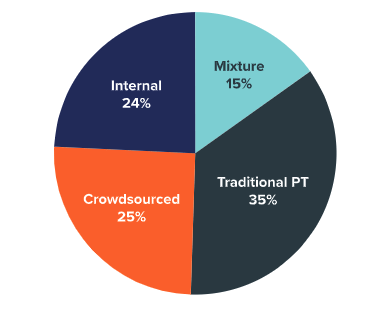
So how often should you be performing penetration tests? Penetration testing should be performed regularly, at least 1-2 times per year. There is also a correlation between the type of testing you do and the frequency you perform penetration tests. 66% of organizations that use traditional penetration testing services test very infrequently, about once per year or less. By contrast, over half of organizations that use crowdsourced testing test at least quarterly. Organizations that test internally are the most frequent testers, with 60% testing at least quarterly.
Penetration testers are an incredible resource, but there aren’t enough in the industry for dozens of testers to work full-time at each organization. This leads to the current models for resourcing talent, such as working through traditional pen test firms and crowdsourcing experts.
It should be noted that more traditional methods of penetration testing are rapidly losing popularity. In 2018, 56% of security leaders reported being dissatisfied with their current pentests. This is for a variety of reasons, such as pentesting firms being inhibited by utilization models, meaning the resume you see isn’t likely to be the talent you get. We’ll cover this more later in this blog post.
What Are the Different Types of Penetration Tests?
There are several types of penetration testing that will help find vulnerabilities hidden across your IT infrastructure. Many organizations use a combination of types to fully cover their needs. These types of tests include:
- Network Security Testing – These help organizations reduce risk and exposure across critical infrastructure within your host network and all network devices.
- Cloud Security Testing – These tests allow you to perform on-demand application security testing in the cloud.
- Web Application Testing – Even with advanced firewalls and vulnerability scanners, web apps continue to harbor more vulnerabilities than any other type of digital asset. These tests help security teams evaluate their constantly-changing, and often highly vulnerable web applications.
- IoT Security Testing – In an increasingly-remote world, IoT and connected device development workflows need protection too. IoT testing allows you to thoroughly test all components of your IoT solution including the web and mobile apps, APIs, hardware, and firmware.
- Social Engineering Testing – This type of testing helps show you employee security, identifying who is following internal training you have in place to protect against phishing or other security threats.
- API Pen Tests – These tests plug into your API development process to provide vulnerability discovery within the forever-multiplying API.
Here at Bugcrowd, we generally split pen testing into two major categories, Classic Pen Test and Next Gen Pen Test. Both include rapid setup and deployment, a 24/7 streaming vulnerability view, SDLC integration, and a flexible API.
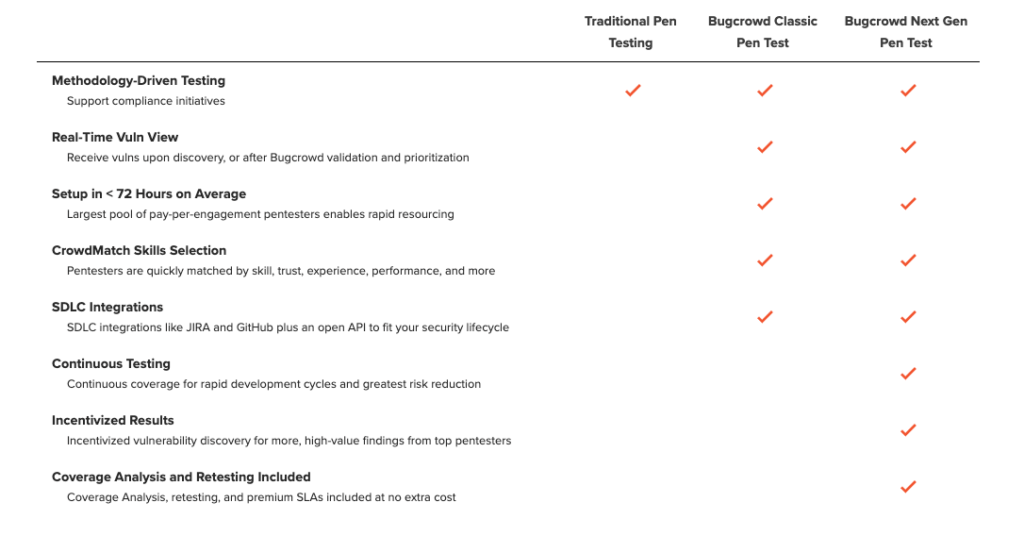
Classic Pen Test provides rapid-access to on-demand methodology-driven testing on a set, per-project rate. Next Gen Pen Test pairs highly vetted and deeply experienced pentesters with organizations that want to incentivize discovery of vulnerabilities to greatly reduce risk, increase go-to-market velocity, and exceed methodology-driven compliance initiatives, all at a lower cost-per-vulnerability. Bugcrowd also offers web application testing, network security testing, IoT security testing, and API pen testing.
What Type of Penetration Test is Best For You?
Now that you have an overview of different penetration testing options, let’s figure out the best option for you and your organization. It might help to understand industry trends. Across all industries and organization sizes, traditional penetration testing services account for just 35% of security testing.
What about the results? 76% of crowdsourced testers received at least 10 vulnerabilities per two-week test, compared to 57% of traditional penetration testing services. The quality of results was also higher. Traditional penetration testing services are twice as likely to deliver a poor result as crowdsourced testing. Internal testing programs performed extremely poorly on both the quality and quantity of results, despite their popularity with enterprises.
As we mentioned earlier in the blog, traditional penetration testing is losing popularity. The lackluster results are one reason for this, but there are a lot of gaps in the traditional penetration testing model, such as:
- Scheduling delays
- Tests are difficult to extend
- Incompatible incentives
- Speed of results
- Questionable skill fit
- Checklist focused
- Point-in-time testing
- Lack of incentive
- Lack of SDLC integration
What about the cost? Traditional penetration testing and crowdsourced testing generally have comparable costs. However, since crowdsourced testing delivers more, higher-quality results, it’s a clear winner for ROI.
Users of crowdsourced security programs benefit from expert skills matching, and those who provide further incentives for valid vulnerabilities report a greater volume of higher-quality vulnerabilities than traditional penetration testing services provide. Crowdsourced testing offers organizations a faster path to compliance without sacrificing the critical insights that help keep products and customers safe. To learn more about penetration testing, check out The Ultimate Guide to Penetration Testing. You can also request a demo to see Bugcrowd’s penetration testing solutions in action.



